What happened to Milw0rm and Packetstorm
Posted: August 20th, 2009 | Author: xanda | Filed under: IT Related | Tags: milw0rm, mubic, packetstorm, str0ke | 2 Comments »Mubic asked:
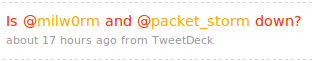
Str0ke said:
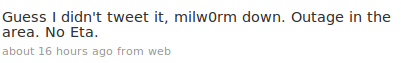
Mubic asked again:
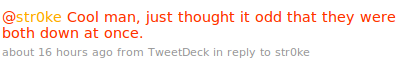
And Str0ke answered:
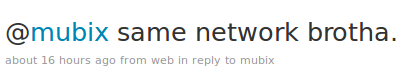
Mubic asked:
Str0ke said:

Mubic asked again:

And Str0ke answered:

ClientMe – Yet Another Client Side Honeypot
It is now in early implementation phase

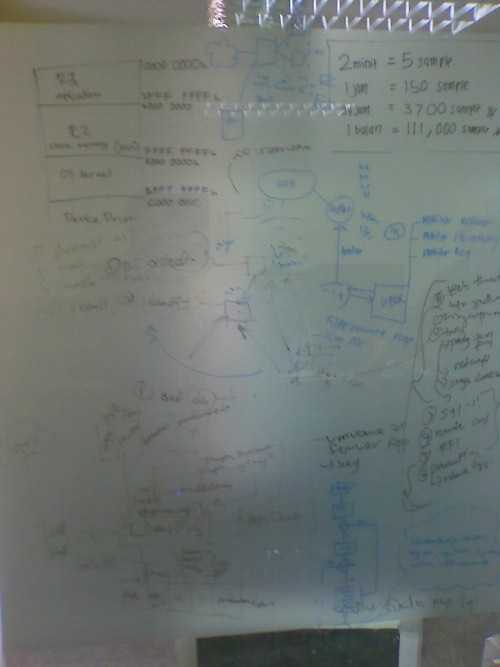


P/S: This project insyaallah will be my master degree’s project at the same time
[updated on 25th August 2009, 11:01PM (GMT +8)]
ClientMe is now in v 0.01 Alpha [see HERE]


dig seems to be OK
I’m still waiting for the news of why this thing happened..
[update]
DAMMIT!! I used “dig facebook.com” and not “dig www.facebook.com”.. ARGH!!!! Anyone has dig result for www.facebook.com? I pretty much believe that it has something to do with Akmai’s distributed servers
[update]
hi all, i believe that, this issues come some the distributed akmai server. If you are on Linux/Unix/Mac, this is what you can do:-
sudo -i echo "69.63.191.219 www.facebook.com" >> /etc/hosts |
then start browsing to facebook 🙂
Title: Facebook privacy: a guide
Author: Jacqui Cheng
Source: Arstechnica
Date Published: 14th August 2009
Excerpt:
….Facebook has decent privacy controls, but most users don’t
realize how to take full advantage of them. Ars guides you through
Facebook’s privacy settings so that you can be both social and
respectable at the same time……
Posted in /dev/project page.
Please refer here: http://www.xanda.org/index.php?page=facebook-privacy-a-guide
Thanks
In last night’s episode of Fox’s thriller show, 24, there is a reference to the Blowfish algorithm which was designed by Bruce Schneier. On the show, an email message that contains the expected location of Jack Bauer is encrypted using Blowfish. The FBI intercepts the message and must decrypt it if they are to find him. I was curious to see what the 24 writers had up their sleeve. The answer: the designer of Blowfish put in a back door which was known to a former CTU operative. The FBI had leverage over the former CTU man because his wife was being held and faced at least 15 years in prison. The cipher was broken in seconds. Thanks a lot, Bruce! Thanks to your back door, Bauer is now being chased as a wanted man … at least until next week.
[Source: Avi Rubin]