PHP-Shell-Detector Bypassed
Posted: August 10th, 2012 | Author: xanda | Filed under: IT Related | 1 Comment »Hi and Ramadan Mubarak to my Muslim friends.
Last few night I saw a twitter update from @pentestit on a project called PHP-Shell-Detector; a php script that helps you find and identify php/cgi(perl)/asp/aspx shells.
My friends and I were a bit disappointed because we have developed the same thing but not yet released to the public for no reason.
But speaking about PHP-Shell-Detector, new stuff still need to be tested 🙂 so I’ve put it into a test
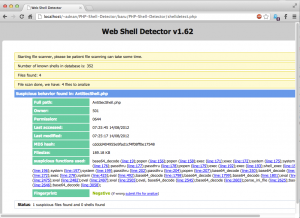
I’ve tested with a webshell I’ve found in the wild. Impressive.. PHP-Shell-Detector managed to detect it. The GUI and ajax was nice as well
I’ve spent some time to take a look at the code and found that the “suspicious functions used” part was implemented with the use of regex and I’ve found that something is missing.. So i’ve created a simple webshell to test my theory. So here is my code:
<?php $cmd = $_GET['cmd']; echo `$cmd`; ?> |
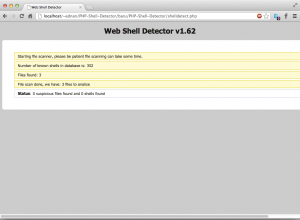
And lets see the result:
This is due to the backtick is not in the regex and I believe it is not in the signature part as well.
I’ve reported this issue on the github page and comeout with the regex and tokenizer suggestion as the solution but from the response that i’ve get, i dont think it will be implemented in this near soon.
Anyway.. As overall, PHP-Shell-Detector is a good project and would help the webmaster to simplify the process of “searching” the hidden planted shell in their website.
Thanks
[Update]
I’ve received an email from the project maintainer saying that the regex has been update. Awesome! 🙂
xanda ni scanner mcm wp jugak kew??scan gunakan keyword $cmd = $_GET[‘cmd’]; base64 n other …
da siap nnty nak pinjam jap… 🙂