Detecting counter.php – The BlackHole Redirector
Posted: April 5th, 2013 | Author: xanda | Filed under: IT Related | No Comments »Have you ever came across the following line of code injected to your (or you visited) website
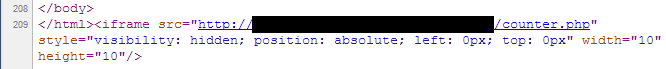
If I get it correctly, it is the BlackHole Exploit Kit redirector.
The pattern for this “counter.php” injected script will always be the same, so for system administrator or webmasters, you can use the following yara rule for your detection
rule counterPHPredirectBHEK
{
meta:
author = "adnan.shukor@gmail.com"
description = "Detection rule to detect compromised page injected with invisible counter.php redirector"
ref = "http://blog.xanda.org/2013/04/05/detecting-counter-php-the-blackhole-redirector"
cve = "NA"
version = "1"
impact = 4
hide = false
strings:
$counterPHP = /\<iframe\ src\=\"https?\:\/\/[a-zA-Z0-9\-\.]{4,260}\/counter\.php\"\ style\=\"visibility\:\ hidden\;\ position\:\ absolute\;\ left\:\ 0px\;\ top\:\ 0px\"\ width\=\"10\"\ height\=\"10\"\/\>$/
condition:
all of them
} |
Thanks
P/S: MyYaraSIG guys, my Macbook is not able to be boot right now, will commit to the repo later
Leave a Reply