Posted: January 12th, 2013 | Author: xanda | Filed under: IT Related | Tags: 0day, CVE-2013-0422, java, yara | 3 Comments »
Hi
It’s a bit to late for me to write this, but at least CVE-2013-0422 is no longer a secret.. and yes I can share some yara rule for this
Anyway, thanks to @kafeine for the disclosure and thanks to Immunity for a very good write up.
So here you go:
rule CVE_2013_0422
{
meta:
description = "Java Applet JMX Remote Code Execution"
cve = "CVE-2013-0422"
ref = "http://pastebin.com/JVedyrCe"
author = "adnan.shukor@gmail.com"
date = "12-Jan-2013"
version = "1"
impact = 4
hide = false
strings:
$0422_1 = "com/sun/jmx/mbeanserver/JmxMBeanServer" fullword
$0422_2 = "com/sun/jmx/mbeanserver/JmxMBeanServerBuilder" fullword
$0422_3 = "com/sun/jmx/mbeanserver/MBeanInstantiator" fullword
$0422_4 = "findClass" fullword
$0422_5 = "publicLookup" fullword
$class = /sun\.org\.mozilla\.javascript\.internal\.(Context|GeneratedClassLoader)/ fullword
condition:
(all of ($0422_*)) or (all of them)
} |
rule CVE_2013_0422
{
meta:
description = "Java Applet JMX Remote Code Execution"
cve = "CVE-2013-0422"
ref = "http://pastebin.com/JVedyrCe"
author = "adnan.shukor@gmail.com"
date = "12-Jan-2013"
version = "1"
impact = 4
hide = false
strings:
$0422_1 = "com/sun/jmx/mbeanserver/JmxMBeanServer" fullword
$0422_2 = "com/sun/jmx/mbeanserver/JmxMBeanServerBuilder" fullword
$0422_3 = "com/sun/jmx/mbeanserver/MBeanInstantiator" fullword
$0422_4 = "findClass" fullword
$0422_5 = "publicLookup" fullword
$class = /sun\.org\.mozilla\.javascript\.internal\.(Context|GeneratedClassLoader)/ fullword
condition:
(all of ($0422_*)) or (all of them)
}
Kindly leave comment I you find ways to improvement this rule. Obfuscation? yeah of course can be used to bypassed this rule as well 😉
Thanks
P/S: MyYaraSIG members should have receive this rule/update earlier today. Just git pull everyone 🙂
Posted: December 12th, 2012 | Author: xanda | Filed under: IT Related | Tags: Exploit Kit, pattern, redkit, regex | 4 Comments »
It’s been a while since the last time I logged in into my WordPress. I’ve jumped on BlueCoat System‘s bandwagon (and left MyCERT earlier), so I’ve to spent some time to make myself familiar with this new environment and job 🙂
Last week, @fknsec, in his blog, wrote a very good article about RedKit Exploit Kit. But here I would like to add few more interesting facts on the RedKit patterns
- @fknsec did mention about “/hmiq.htm” in his blog, but from my observation, beside Porche and Ferari, the RedKit author also like the letter H. The naming convention for the HTML file will always start from H and ended with .htm (everything in small case). So a working regex for this pattern world be:
** updated on 14 Feb 2013 **
Look like this portion is no longer valid at the moment. You can replace it with:
- 887.jar and 332.jar is quite unique to RedKit. Go hunt them!
- Same goes to 987.pdf
- c.htm as mentioned by @fknsec can be in 1 char (letter) file name (in small case), or it can also be in 2 digit (number) and ended with .htm.
/\/([a-z]{1}|\d{2})\.htm$/ |
/\/([a-z]{1}|\d{2})\.htm$/
- Unlike BlackHole and Cool exploit kit, RedKit will usually be hosted on compromised websites and not having his own special subdomain. Most of the time, RedKit files will be in the main directory of a website/domain
- From my observation, among the famous tricks to lure victim to RedKit are:
- Redirector script planted in jquery JS file
- Redirector in “Domain to sell” placeholder
I think that’s all for today. I don’t know when is the next time to update my blog, since will keep my self busy in these coming weeks, with my first baby is going to execute /h(is|er)/ first version of “Hello World” script in near soon.
Till then, stay safe everyone & happy hunting!
Reference:
- http://fortknoxnetworks.blogspot.com/2012/12/exploit-medfos-url-detection-with-drop.html
- http://malware.dontneedcoffee.com/2012/08/cve-2012-4681-redkit-exploit-kit-i-want.html
Posted: October 20th, 2012 | Author: xanda | Filed under: IT Related | 2 Comments »
I’m not sure for the terms used in the title, but what I’m trying to say is..
- We are familiar with this:
- And this:
- But, what about:
- And also:
- And this:
- And..
It’s not over yet. Find out more at:
- https://hackvertor.co.uk/hvurl/3x
- http://www.pc-help.org/obscure.htm
Please leave your comment with additional awesome example 🙂
Posted: October 20th, 2012 | Author: xanda | Filed under: IT Related | No Comments »
It’s been a while since the last update. What a busy weeks..
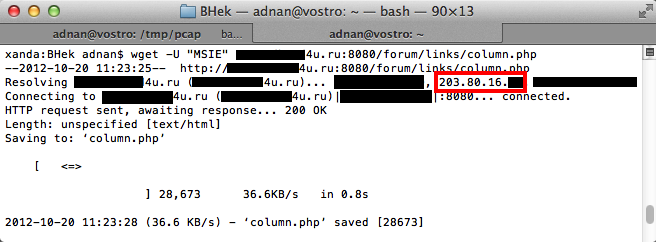
I’ve subscribed to MalwareDomainList‘s RSS and recently I’ve found a couple of entries on BlackHole Exploit Kit hosted in Malaysia. I’ve performed a quick analysis on the domains and found that, it is confirmed serving BlackHole Exploit Kit v2.0.
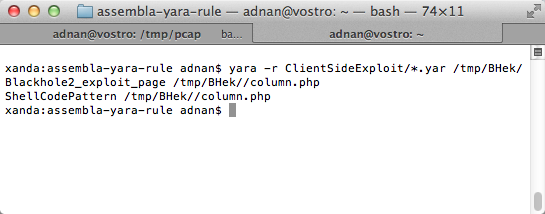
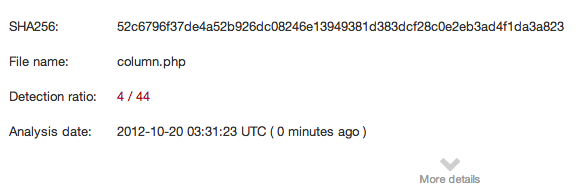
And as for the detection rate in Virustotal: 4/44
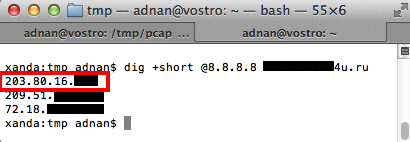
I’ve done a quick analysis on the IP using robtex and hostmap, there are 12 (or more) .RU domain associated with the IP. Most of the domains store multiple A record for their DNS. 2 of the IPs are in US, and 1 in Malaysian Research & Education Network.

Posted: October 2nd, 2012 | Author: xanda | Filed under: IT Related | Tags: Android, exabytes, redkit, samsung, USSD | No Comments »
What a busy week so here is my late update.
I’ve been asked by my wife on this weird javascript pattern. I’m not managed to download the content of the php file due to it has been removed, and some of them were giving me infinite loop of 302. Someone tweet me and ask me to set the referrer as the URL of the ‘infected’ website. A few hours later, I’ve saw a blog post “Redkit Exploit Kit: upgrades in anti-forensics.” popping up from my RSS reader. Mystery solved!
You might have heard about remote USSD attack has been discussed last week. This ‘vulnerability’ exist due to improper handling of “tel:” URi in Android. It affects many phones and according to this entry, it has been verified on not only Samsung Galaxy S3, but also on an HTC One X (running HTC Sense 4.0 on Android 4.0.3) and a Motorola Defy (running Cyanogen Mod 7 on Android 2.3.5). Patch has been released to address this issue and Android 4.1 has been verified not vulnerable to this vulnerability. Alternatively, users can use TelStop or Auto-Reset Blocker to prevent tel URi to be executed without user prompt.
A little update from Malaysia landscape. Exabytes has announced that their cloud server has been compromised and some virtual machines and data have been deleted. Official announcement can be found here.
Thats all.. Stay safe




