Posted: May 7th, 2024 | Author: xanda | Filed under: IT Related | No Comments »

Imagine receiving an urgent SMS claiming to be from your bank. The message informs you that your credit card has been used for a suspicious transaction. To verify or dispute the charges, you’re instructed to call a provided phone number. Sounds familiar, right? No?

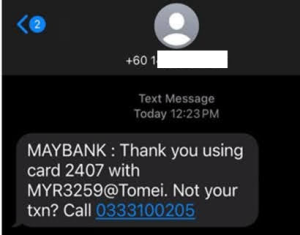
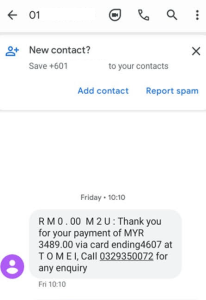
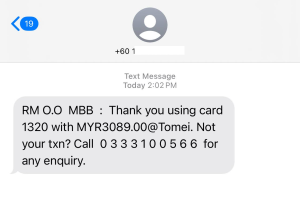
The SMS messages were sent from regular mobile phone numbers, not short code senders. Now, take a look at the phone numbers included in the SMS—they do not belong to the bank. Wait, look closely… What a neat sequence. Coincidence? :
- 0333100144
- 0333100566
- 0333100205
- 0329350072
- 0329350078
Earlier this morning, I decided to investigate further. I dialed the suspicious phone number, 0329350078, to understand the scammer’s modus operandi. To my surprise, an IVR system answered, claiming to represent Maybank. I selected the option to “report a suspicious transaction”, and the call was “transferred” to a real person. The person tried to convince me that my card and account had been hacked, and that it would be better to transfer the money to a third-party account before the account was frozen. I was eager to continue the conversation; however, I had a meeting to attend, so I terminated the call.
Later, around 6 p.m., I attempted to contact the same number once more, only to find it unreachable. Subsequently, I tried several other phone numbers, all of which proved to be similarly inaccessible.
A brief inquiry into the reputation (some) of these numbers suggests their involvement in shady activities over an extended period. While my intuition has provided some clues about the owners, I am not donning my investigative hat today, akin to Brian Krebs. Therefore, no disclosures will be made in this post.
Here are some advisory insights for awareness
How does it work:
- Victims receive an SMS claiming to be from a bank or financial institution
- The message typically warns of suspicious transactions on their account and provides a phone number to call
- When victims call the number, they are directed to an Interactive Voice Response (IVR) system that mimics the bank’s
- official system
- After selecting the option to report a suspicious transaction, victims are transferred to a real person who attempts to extract personal information or convince them to transfer money to a “safe account”
How to spot it:
- Be cautious if you receive unsolicited SMS messages related to your bank account/transaction – especially from normal mobile phone number. Banks will usually use short code SMS providers.
- Look for poor grammar, inconsistent formatting/spacing or spelling errors in the message (if any)
- Avoid clicking on any links provided in the SMS (URLs in SMS messages are now blocked in Malaysia, except when sent from a short code sender)
Protecting Yourself: Tips and Awareness
- Stay Informed: Be aware of common scams and their modus operandi. Familiarize yourself with the tactics fraudsters use to deceive victims.
- Verify Communications: If you receive an SMS or call related to your bank account, verify its legitimacy independently. Do not rely solely on the information provided in the message.
- Report Suspicious Activity: If you encounter a suspicious SMS or call, report it to your bank and NSRC (997) immediately.
- Educate Others: Share this information with family and friends to help them stay vigilant against scams.
Stay alert and safeguard yourself from falling prey to scams.
Posted: April 29th, 2024 | Author: xanda | Filed under: IT Related, Project | No Comments »
So, in my last blog post, you might’ve spotted something a bit different – an unintentional experiment with automation and LLM. Yep, it caught me off guard too.
But you know what? Despite the surprise, it got me thinking. And after a closer look, it turns out there’s something here worth exploring.
Seems like I can generate a “daily bulletin” using this method. So, I’m thinking of sticking with it for a while.
But let’s keep it real – human input is still crucial.
I’m open to your thoughts and suggestions. Any ideas on how to make this better? Just drop me a line.
Posted: April 28th, 2024 | Author: xanda | Filed under: IT Related | No Comments »

In recent years, Malaysia has witnessed a surge in “SMS” phishing (also known as smishing) attacks. These deceptive messages target unsuspecting individuals via text messages, luring them into revealing sensitive information or clicking on malicious links. Let’s delve into the key aspects of this growing threat:
1. The Prevalence of SMS Phishing
According to a survey conducted by international market research firm Ipsos, more than two-thirds of Malaysians (76%) have encountered scams at some point in their lives. Among the communication channels exploited by scammers, phone calls and WhatsApp applications take the lead. SMS phishing accounts for a significant portion, with 56% of respondents reporting such incidents. The remaining channels include Facebook (31%), Telegram (30%), and SMS text (29%).
2. Evolving Tactics
The modus operandi of SMS phishing has evolved over time. Initially, scammers targeted traditional SMS messages, but as telcos in Malaysia began blocking SMS containing URLs, fraudsters adapted. Recent campaigns have shifted focus to Apple iMessage and Android RCS (Rich Communication Services), which technically aren’t SMS but operate within similar messaging platforms. Additionally, spoofed SMS via fake base transceiver stations (BTS) have emerged, further complicating the landscape.
3. The TNG eWallet Scam
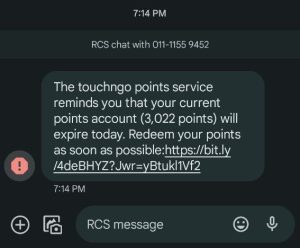
Recently, the theme of SMS phishing has shifted from parcel services and telco-related scams to TNG eWallet. Victims receive messages claiming that their loyalty points are about to expire, urging them to redeem by clicking a link. However, these links lead to fraudulent websites designed to steal personal information, including campaigns aimed at hijacking Telegram accounts. The shift to TNG eWallet reflects scammers’ adaptability and their ability to exploit popular services.
4. Reporting and Awareness
Despite the prevalence of SMS phishing, fewer than half of victims report the incidents to authorities. The police receive the majority of complaints (62%), while other agencies like the Malaysian Communications and Multimedia Commission (MCMC), CyberSecurity Malaysia, and Bank Negara Malaysia receive fewer reports. Raising awareness and empowering the public with education and digital safeguards are crucial steps in combating this menace.
5. Indicators of Compromise
Indicators of Compromise (IOCs) for the latest campaign should include relevant and enriched indicators:
touchngo-z.top
globeih.top
globein.top
telkomsel-og.top
telkomsel-oj.top
maxis-l.top
globeig.top
emag-k.top
telkomsel-om.top
telkomsel-ok.top
ais-g.top
ais-h.top
ais-f.top
ais-d.top
globeij.top
etisalat-z.top
telkomsel-oz.top
telkomsel-on.top
telkomsel-ox.top
telkomsel-ov.top
telkomsel-os.top
telkomsel-oq.top
telkomsel-id.com
dpd-a.top
emag-q.top
dpd-c.xyz
dpd-a.vip
globeif.top
globeiv.top
globeix.top
globeid.top
globeia.top
globeic.top
globeiz.top
globeib.top
globeis.top
emag-w.top
telkomseip.top
telkomseie.top
telkomseit.top
telkomseiw.top
telkomsexx.top
telkomseiq.top
telkomseir.top
telkomseiy.top
telkomsexz.top
telkomsexc.top
telkomseio.top
telkomsexv.top
telkomseiu.top
maltapost-x.top
telkomselia.top
telkomselic.top
cambodiapostv.top
telkomselim.top
telkomselil.top
telkomselib.top
telkomselik.top
telkomselij.top
ais-j.top
telkomselin.top |
touchngo-z.top
globeih.top
globein.top
telkomsel-og.top
telkomsel-oj.top
maxis-l.top
globeig.top
emag-k.top
telkomsel-om.top
telkomsel-ok.top
ais-g.top
ais-h.top
ais-f.top
ais-d.top
globeij.top
etisalat-z.top
telkomsel-oz.top
telkomsel-on.top
telkomsel-ox.top
telkomsel-ov.top
telkomsel-os.top
telkomsel-oq.top
telkomsel-id.com
dpd-a.top
emag-q.top
dpd-c.xyz
dpd-a.vip
globeif.top
globeiv.top
globeix.top
globeid.top
globeia.top
globeic.top
globeiz.top
globeib.top
globeis.top
emag-w.top
telkomseip.top
telkomseie.top
telkomseit.top
telkomseiw.top
telkomsexx.top
telkomseiq.top
telkomseir.top
telkomseiy.top
telkomsexz.top
telkomsexc.top
telkomseio.top
telkomsexv.top
telkomseiu.top
maltapost-x.top
telkomselia.top
telkomselic.top
cambodiapostv.top
telkomselim.top
telkomselil.top
telkomselib.top
telkomselik.top
telkomselij.top
ais-j.top
telkomselin.top
Posted: June 12th, 2023 | Author: xanda | Filed under: IT Related | No Comments »
Top 5 source of IPs for few protocols, hitting my honeypot last week (5-11 June 2023)
Apache:
153,143.110.222.166
143,77.68.98.209
127,80.211.51.121
127,54.36.102.11
127,182.16.248.237 |
153,143.110.222.166
143,77.68.98.209
127,80.211.51.121
127,54.36.102.11
127,182.16.248.237
SSH:
1757,180.242.128.226
1008,179.166.57.219
670,202.161.190.82
246,171.244.53.224
164,57.128.113.49 |
1757,180.242.128.226
1008,179.166.57.219
670,202.161.190.82
246,171.244.53.224
164,57.128.113.49
DNS:
17,47.100.101.182
4,71.6.199.23
3,45.128.232.145
3,185.94.111.1
3,152.32.200.113 |
17,47.100.101.182
4,71.6.199.23
3,45.128.232.145
3,185.94.111.1
3,152.32.200.113
Few IPs observed coming from Malaysian ISP
4788 | 210.187.80.132 | TMNET-AS-AP TM Net, Internet Service Provider, MY
9930 | 211.24.12.162 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
9930 | 211.25.119.142 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
23678 | 27.131.36.170 | MYKRIS-AS-MY Mykris Asia, Managed Network and Service Provider, MY |
4788 | 210.187.80.132 | TMNET-AS-AP TM Net, Internet Service Provider, MY
9930 | 211.24.12.162 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
9930 | 211.25.119.142 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
23678 | 27.131.36.170 | MYKRIS-AS-MY Mykris Asia, Managed Network and Service Provider, MY
If you like to see the complete data captured within last week, you may visit the github page
Posted: December 14th, 2021 | Author: xanda | Filed under: IT Related | Tags: antivirus, CVE-2021-4428, JndiLookup, log4j, log4j-core | 1 Comment »
In my previous post, I did share a bash script to help you to search for vulnerable log4j and delete the JndiLookup.class
When it come to Windows, it became a bit tricky because zip command/cli is not there and make it a bit difficult for massive deployment. However, today I’ve experimented with Antivirus(es) solution to perform search of the vulnerable log4j (or inventory purposes) and to apply mitigation by removing the JndiLookup.class
For inventory purposes, you may use the hashes of the vulnerable log4j below as custom indicator in your antivirus solution, in audit mode (not block/delete mode) and perform scanning. Whenever you receive alert from this custom rule, you know which machine are running the vulnerable version and may plan for the next action from there.
While for “auto mitigation”, you may use the hashes of the vulnerable JndiLookup.class below as custom indicator in your antivirus solution, in block/delete mode and perform scanning. Antivirus will be able to parse the JAR (zip) file and delete on specific hashes (JndiLookup.class) while ignoring other files. As per my testing with Microsoft Defender, Kaspersky, and Symantec SEP, only the specific hash/file will be remove and the JAR (zip) file will not be deleted. However it might be different for different configuration and please consult your antivirus vendor for confirmation
Hope it helps. Good luck and all the best
Vulnerable Log4j hashes:
Log4j JAR version,md5,sha1,sha256
log4j-core-2.0-beta9.jar,152ecb3ce094ac5bc9ea39d6122e2814,678861ba1b2e1fccb594bb0ca03114bb05da9695,dcde6033b205433d6e9855c93740f798951fa3a3f252035a768d9f356fde806d
log4j-core-2.0-rc1.jar,088df113ad249ab72bf19b7f00b863d5,4363cdf913a584fe8fa72cf4c0eaae181ef7d1eb,db3906edad6009d1886ec1e2a198249b6d99820a3575f8ec80c6ce57f08d521a
log4j-core-2.0-rc2.jar,de8d01cc15fd0c74fea8bbb668e289f5,2e8d52acfc8c2bbbaa7baf9f3678826c354f5405,ec411a34fee49692f196e4dc0a905b25d0667825904862fdba153df5e53183e0
log4j-core-2.0.jar,cd70a1888ecdd311c1990e784867ce1e,7621fe28ce0122d96006bdb56c8e2cfb2a3afb92,85338f694c844c8b66d8a1b981bcf38627f95579209b2662182a009d849e1a4c
log4j-core-2.0.1.jar,fbfa5f33ab4b29a6fdd52473ee7b834d,895130076efaf6dcafb741ed7e97f2d346903708,a00a54e3fb8cb83fab38f8714f240ecc13ab9c492584aa571aec5fc71b48732d
log4j-core-2.0.2.jar,8c0cf3eb047154a4f8e16daf5a209319,13521c5364501478e28c77a7f86b90b6ed5dbb77,c584d1000591efa391386264e0d43ec35f4dbb146cad9390f73358d9c84ee78d
log4j-core-2.1.jar,8d331544b2e7b20ad166debca2550d73,31823dcde108f2ea4a5801d1acc77869d7696533,8bdb662843c1f4b120fb4c25a5636008085900cdf9947b1dadb9b672ea6134dc
log4j-core-2.2.jar,5e4bca5ed20b94ab19bb65836da93f96,c707664e020218f8529b9a5e55016ee15f0f82ac,c830cde8f929c35dad42cbdb6b28447df69ceffe99937bf420d32424df4d076a
log4j-core-2.3.jar,110ab3e3e4f3780921e8ee5dde3373ad,58a3e964db5307e30650817c5daac1e8c8ede648,6ae3b0cb657e051f97835a6432c2b0f50a651b36b6d4af395bbe9060bb4ef4b2
log4j-core-2.4.jar,0079c907230659968f0fc0e41a6abcf9,0d99532ba3603f27bebf4cdd3653feb0e0b84cf6,535e19bf14d8c76ec00a7e8490287ca2e2597cae2de5b8f1f65eb81ef1c2a4c6
log4j-core-2.4.1.jar,f0c43adaca2afc71c6cc80f851b38818,a5334910f90944575147fd1c1aef9f407c24db99,42de36e61d454afff5e50e6930961c85b55d681e23931efd248fd9b9b9297239
log4j-core-2.5.jar,dd0e3e0b404083ec69618aabb50b8ac0,7ed845de1dfe070d43511fab321784e6c4118398,4f53e4d52efcccdc446017426c15001bb0fe444c7a6cdc9966f8741cf210d997
log4j-core-2.6.jar,5523f144faef2bfca08a3ca8b2becd6a,a7cb258b9c36f49c148834a3a35b53fe73c28777,df00277045338ceaa6f70a7b8eee178710b3ba51eac28c1142ec802157492de6
log4j-core-2.6.1.jar,48f7f3cda53030a87e8c387d8d1e4265,2b557bf1023c3a3a0f7f200fafcd7641b89cbb83,28433734bd9e3121e0a0b78238d5131837b9dbe26f1a930bc872bad44e68e44e
log4j-core-2.6.2.jar,472c8e1fbaa0e61520e025c255b5d168,00a91369f655eb1639c6aece5c5eb5108db18306,cf65f0d33640f2cd0a0b06dd86a5c6353938ccb25f4ffd14116b4884181e0392
log4j-core-2.7.jar,2b63e0e5063fdaccf669a1e26384f3fd,a3f2b4e64c61a7fc1ed8f1e5ba371933404ed98a,5bb84e110d5f18cee47021a024d358227612dd6dac7b97fa781f85c6ad3ccee4
log4j-core-2.8.jar,c6d233bc8e9cfe5da690059d27d9f88f,2be463a710be42bb6b4831b980f0d270b98ff233,ccf02bb919e1a44b13b366ea1b203f98772650475f2a06e9fac4b3c957a7c3fa
log4j-core-2.8.1.jar,547bb3ed2deb856d0e3bbd77c27b9625,4ac28ff2f1ddf05dae3043a190451e8c46b73c31,815a73e20e90a413662eefe8594414684df3d5723edcd76070e1a5aee864616e
log4j-core-2.8.2.jar,4a5177a172764bda6f4472b94ba17ccb,979fc0cf8460302e4ffbfe38c1b66a99450b0bb7,10ef331115cbbd18b5be3f3761e046523f9c95c103484082b18e67a7c36e570c
log4j-core-2.9.0.jar,fab646257f945b0b2a7ce3e1c3e3ce5f,052f6548ae1688e126c29b5dc400929dc0128615,fb086e42c232d560081d5d76b6b9e0979e5693e5de76734cad5e396dd77278fd
log4j-core-2.9.1.jar,942f429eacb8015e18d8f59996cfbee6,c041978c686866ee8534f538c6220238db3bb6be,dc435b35b5923eb05afe30a24f04e9a0a5372da8e76f986efe8508b96101c4ff
log4j-core-2.10.0.jar,dc99011f047e63dcc741b5ab68d116db,c90b597163cd28ab6d9687edd53db601b6ea75a1,22b58febab566eddd5d4863f09dad4d5cc57677b6d4be745e3c6ce547124a66d
log4j-core-2.11.0.jar,2abec2ce665e0d529a3f28fffbbb2dd3,e6b751e02120c08702d98750f6a80bc25343b7f5,c32029b32da3d8cf2feca0790a4bc2331ea7eb62ab368a8980b90c7d8c8101e0
log4j-core-2.11.1.jar,b2242de0677be6515d6cefbf48e7e5d5,592a48674c926b01a9a747c7831bcd82a9e6d6e4,a20c34cdac4978b76efcc9d0db66e95600bd807c6a0bd3f5793bcb45d07162ec
log4j-core-2.11.2.jar,c8bd8b5c5aaaa07a3dcbf57de01c9266,6c2fb3f5b7cd27504726aef1b674b542a0c9cf53,d4748cd5d8d67f513de7634fa202740490d7e0ab546f4bf94e5c4d4a11e3edbc
log4j-core-2.12.0.jar,5c527821d1084a7ef3e03d40144ff532,01723837573e4c5dbc8840f9f6e8f79b245b94bb,8818f82570d3f509cfb27c209b9a8df6f188857b7462951a61a137be09cf3463
log4j-core-2.12.1.jar,0138ba1c191d5c754fd0e3c3a61c0307,4382e93136c06bfb34ddfa0bb8a9fb4ea2f3df59,885e31a14fc71cb4849e93564d26a221c685a789379ef63cb2d082cedf3c2235
log4j-core-2.13.0.jar,b71a13fd5df251694fca116240003b22,57b8b57dac4c87696acb4b8457fd8cbf4273d40d,82e91afe0c5628b32ae99dd6965878402c668773fbd49b45b2b8c06a426c5bbb
log4j-core-2.13.1.jar,d365e48221414f93feef093a1bf607ef,533f6ae0bb0ce091493f2eeab0c1df4327e46ef1,88ebd503b35a0debe18c2707db9de33a8c6d96491270b7f02dd086b8072426b2
log4j-core-2.13.2.jar,0ac5b3e6e69ba7765683798e669a30b2,8eb1fc1914eb2550bf3ddea26917c9a7cbb00593,268dc17d3739992d4d1ca2c27f94630fb203a40d07e9ad5dfae131d4e3fa9764
log4j-core-2.13.3.jar,cc7d55ed69cc5fd34035b15c6edf79a0,4e857439fc4fe974d212adaaaa3b118b8b50e3ec,9529c55814264ab96b0eeba2920ac0805170969c994cc479bd3d4d7eb24a35a8
log4j-core-2.14.0.jar,862c00b2e854f9c0f1e8d8409d23d899,e257b0562453f73eabac1bc3181ba33e79d193ed,f04ee9c0ac417471d9127b5880b96c3147249f20674a8dbb88e9949d855382a8
log4j-core-2.14.1.jar,948dda787593340a7af1a18e328b7b7f,9141212b8507ab50a45525b545b39d224614528b,ade7402a70667a727635d5c4c29495f4ff96f061f12539763f6f123973b465b0 |
Log4j JAR version,md5,sha1,sha256
log4j-core-2.0-beta9.jar,152ecb3ce094ac5bc9ea39d6122e2814,678861ba1b2e1fccb594bb0ca03114bb05da9695,dcde6033b205433d6e9855c93740f798951fa3a3f252035a768d9f356fde806d
log4j-core-2.0-rc1.jar,088df113ad249ab72bf19b7f00b863d5,4363cdf913a584fe8fa72cf4c0eaae181ef7d1eb,db3906edad6009d1886ec1e2a198249b6d99820a3575f8ec80c6ce57f08d521a
log4j-core-2.0-rc2.jar,de8d01cc15fd0c74fea8bbb668e289f5,2e8d52acfc8c2bbbaa7baf9f3678826c354f5405,ec411a34fee49692f196e4dc0a905b25d0667825904862fdba153df5e53183e0
log4j-core-2.0.jar,cd70a1888ecdd311c1990e784867ce1e,7621fe28ce0122d96006bdb56c8e2cfb2a3afb92,85338f694c844c8b66d8a1b981bcf38627f95579209b2662182a009d849e1a4c
log4j-core-2.0.1.jar,fbfa5f33ab4b29a6fdd52473ee7b834d,895130076efaf6dcafb741ed7e97f2d346903708,a00a54e3fb8cb83fab38f8714f240ecc13ab9c492584aa571aec5fc71b48732d
log4j-core-2.0.2.jar,8c0cf3eb047154a4f8e16daf5a209319,13521c5364501478e28c77a7f86b90b6ed5dbb77,c584d1000591efa391386264e0d43ec35f4dbb146cad9390f73358d9c84ee78d
log4j-core-2.1.jar,8d331544b2e7b20ad166debca2550d73,31823dcde108f2ea4a5801d1acc77869d7696533,8bdb662843c1f4b120fb4c25a5636008085900cdf9947b1dadb9b672ea6134dc
log4j-core-2.2.jar,5e4bca5ed20b94ab19bb65836da93f96,c707664e020218f8529b9a5e55016ee15f0f82ac,c830cde8f929c35dad42cbdb6b28447df69ceffe99937bf420d32424df4d076a
log4j-core-2.3.jar,110ab3e3e4f3780921e8ee5dde3373ad,58a3e964db5307e30650817c5daac1e8c8ede648,6ae3b0cb657e051f97835a6432c2b0f50a651b36b6d4af395bbe9060bb4ef4b2
log4j-core-2.4.jar,0079c907230659968f0fc0e41a6abcf9,0d99532ba3603f27bebf4cdd3653feb0e0b84cf6,535e19bf14d8c76ec00a7e8490287ca2e2597cae2de5b8f1f65eb81ef1c2a4c6
log4j-core-2.4.1.jar,f0c43adaca2afc71c6cc80f851b38818,a5334910f90944575147fd1c1aef9f407c24db99,42de36e61d454afff5e50e6930961c85b55d681e23931efd248fd9b9b9297239
log4j-core-2.5.jar,dd0e3e0b404083ec69618aabb50b8ac0,7ed845de1dfe070d43511fab321784e6c4118398,4f53e4d52efcccdc446017426c15001bb0fe444c7a6cdc9966f8741cf210d997
log4j-core-2.6.jar,5523f144faef2bfca08a3ca8b2becd6a,a7cb258b9c36f49c148834a3a35b53fe73c28777,df00277045338ceaa6f70a7b8eee178710b3ba51eac28c1142ec802157492de6
log4j-core-2.6.1.jar,48f7f3cda53030a87e8c387d8d1e4265,2b557bf1023c3a3a0f7f200fafcd7641b89cbb83,28433734bd9e3121e0a0b78238d5131837b9dbe26f1a930bc872bad44e68e44e
log4j-core-2.6.2.jar,472c8e1fbaa0e61520e025c255b5d168,00a91369f655eb1639c6aece5c5eb5108db18306,cf65f0d33640f2cd0a0b06dd86a5c6353938ccb25f4ffd14116b4884181e0392
log4j-core-2.7.jar,2b63e0e5063fdaccf669a1e26384f3fd,a3f2b4e64c61a7fc1ed8f1e5ba371933404ed98a,5bb84e110d5f18cee47021a024d358227612dd6dac7b97fa781f85c6ad3ccee4
log4j-core-2.8.jar,c6d233bc8e9cfe5da690059d27d9f88f,2be463a710be42bb6b4831b980f0d270b98ff233,ccf02bb919e1a44b13b366ea1b203f98772650475f2a06e9fac4b3c957a7c3fa
log4j-core-2.8.1.jar,547bb3ed2deb856d0e3bbd77c27b9625,4ac28ff2f1ddf05dae3043a190451e8c46b73c31,815a73e20e90a413662eefe8594414684df3d5723edcd76070e1a5aee864616e
log4j-core-2.8.2.jar,4a5177a172764bda6f4472b94ba17ccb,979fc0cf8460302e4ffbfe38c1b66a99450b0bb7,10ef331115cbbd18b5be3f3761e046523f9c95c103484082b18e67a7c36e570c
log4j-core-2.9.0.jar,fab646257f945b0b2a7ce3e1c3e3ce5f,052f6548ae1688e126c29b5dc400929dc0128615,fb086e42c232d560081d5d76b6b9e0979e5693e5de76734cad5e396dd77278fd
log4j-core-2.9.1.jar,942f429eacb8015e18d8f59996cfbee6,c041978c686866ee8534f538c6220238db3bb6be,dc435b35b5923eb05afe30a24f04e9a0a5372da8e76f986efe8508b96101c4ff
log4j-core-2.10.0.jar,dc99011f047e63dcc741b5ab68d116db,c90b597163cd28ab6d9687edd53db601b6ea75a1,22b58febab566eddd5d4863f09dad4d5cc57677b6d4be745e3c6ce547124a66d
log4j-core-2.11.0.jar,2abec2ce665e0d529a3f28fffbbb2dd3,e6b751e02120c08702d98750f6a80bc25343b7f5,c32029b32da3d8cf2feca0790a4bc2331ea7eb62ab368a8980b90c7d8c8101e0
log4j-core-2.11.1.jar,b2242de0677be6515d6cefbf48e7e5d5,592a48674c926b01a9a747c7831bcd82a9e6d6e4,a20c34cdac4978b76efcc9d0db66e95600bd807c6a0bd3f5793bcb45d07162ec
log4j-core-2.11.2.jar,c8bd8b5c5aaaa07a3dcbf57de01c9266,6c2fb3f5b7cd27504726aef1b674b542a0c9cf53,d4748cd5d8d67f513de7634fa202740490d7e0ab546f4bf94e5c4d4a11e3edbc
log4j-core-2.12.0.jar,5c527821d1084a7ef3e03d40144ff532,01723837573e4c5dbc8840f9f6e8f79b245b94bb,8818f82570d3f509cfb27c209b9a8df6f188857b7462951a61a137be09cf3463
log4j-core-2.12.1.jar,0138ba1c191d5c754fd0e3c3a61c0307,4382e93136c06bfb34ddfa0bb8a9fb4ea2f3df59,885e31a14fc71cb4849e93564d26a221c685a789379ef63cb2d082cedf3c2235
log4j-core-2.13.0.jar,b71a13fd5df251694fca116240003b22,57b8b57dac4c87696acb4b8457fd8cbf4273d40d,82e91afe0c5628b32ae99dd6965878402c668773fbd49b45b2b8c06a426c5bbb
log4j-core-2.13.1.jar,d365e48221414f93feef093a1bf607ef,533f6ae0bb0ce091493f2eeab0c1df4327e46ef1,88ebd503b35a0debe18c2707db9de33a8c6d96491270b7f02dd086b8072426b2
log4j-core-2.13.2.jar,0ac5b3e6e69ba7765683798e669a30b2,8eb1fc1914eb2550bf3ddea26917c9a7cbb00593,268dc17d3739992d4d1ca2c27f94630fb203a40d07e9ad5dfae131d4e3fa9764
log4j-core-2.13.3.jar,cc7d55ed69cc5fd34035b15c6edf79a0,4e857439fc4fe974d212adaaaa3b118b8b50e3ec,9529c55814264ab96b0eeba2920ac0805170969c994cc479bd3d4d7eb24a35a8
log4j-core-2.14.0.jar,862c00b2e854f9c0f1e8d8409d23d899,e257b0562453f73eabac1bc3181ba33e79d193ed,f04ee9c0ac417471d9127b5880b96c3147249f20674a8dbb88e9949d855382a8
log4j-core-2.14.1.jar,948dda787593340a7af1a18e328b7b7f,9141212b8507ab50a45525b545b39d224614528b,ade7402a70667a727635d5c4c29495f4ff96f061f12539763f6f123973b465b0
Vulnerable JndiLookup.class hashes:
JndiLookup.class for Log4J version,md5sum,sha1sum,sha256sum
2.0-beta9,662118846c452c4973eca1057859ad61,9799470c2cca80f047f6b0d1588dacae9aae26fc,39a495034d37c7934b64a9aa686ea06b61df21aa222044cc50a47d6903ba1ca8
2.0-rc1,662118846c452c4973eca1057859ad61,9799470c2cca80f047f6b0d1588dacae9aae26fc,39a495034d37c7934b64a9aa686ea06b61df21aa222044cc50a47d6903ba1ca8
2.0-rc2,1daf21d95a208cfce994704824f46fae,ec9326bae452f2d2e8a4852b24799d6458d11d46,a03e538ed25eff6c4fe48aabc5514e5ee687542f29f2206256840e74ed59bcd2
2,62c82ad7c1ec273a683de928c93abbe9,e605ca8be62f8f26c43d906f392090231e96edfd,fd6c63c11f7a6b52eff04be1de3477c9ddbbc925022f7216320e6db93f1b7d29
2.0.1,2365c12b4a7c5fa5d7903dd90ca9e463,040c7583735f58988635563b0b6c0f009d5ae5c0,964fa0bf8c045097247fa0c973e0c167df08720409fd9e44546e0ceda3925f3e
2.0.2,5c727238e74ffac28315c36df27ef7cc,7d403e7e7208e4d9ebaf2b32ddc90a04170580c5,9626798cce6abd0f2ffef89f1a3d0092a60d34a837a02bbe571dbe00236a2c8c
2.1,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.2,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.3,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.4,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.4.1,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.5,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.6,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.6.1,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.6.2,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.7,4618c4bea52a4e2e2693b7d91b019c71,9d62849523dc3efbbe8b289e34f7cd84a6c37275,cee2305065bb61d434cdb45cfdaa46e7da148e5c6a7678d56f3e3dc8d7073eae
2.8,fe963defc63d2df86d3d4e2f160939ab,2e81d183edf1a8951b13a2f62de86e71d97e0d14,66c89e2d5ae674641138858b571e65824df6873abb1677f7b2ef5c0dd4dbc442
2.8.1,fe963defc63d2df86d3d4e2f160939ab,2e81d183edf1a8951b13a2f62de86e71d97e0d14,66c89e2d5ae674641138858b571e65824df6873abb1677f7b2ef5c0dd4dbc442
2.8.2,641fd7ae76e95b35f02c55ffbf430e6b,f5f55d34272b0ed9971943c35857dbca092c990f,d4ec57440cd6db6eaf6bcb6b197f1cbaf5a3e26253d59578d51db307357cbf15
2.9.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.9.1,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.10.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.1,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.2,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.12.0,4cb3a0271f77c02fd2de3144a729ab70,1dee0b0a29a7a2c13d4a7a12374038616cc1de89,5c104d16ff9831b456e4d7eaf66bcf531f086767782d08eece3fb37e40467279
2.12.1,4cb3a0271f77c02fd2de3144a729ab70,1dee0b0a29a7a2c13d4a7a12374038616cc1de89,5c104d16ff9831b456e4d7eaf66bcf531f086767782d08eece3fb37e40467279
2.13.0,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.1,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.2,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.3,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.14.0,737b430fac6caef7c485c9c47f0f9104,3aeb386c7ada3bd936bc20698b6d64e4e1643293,84057480ba7da6fb6d9ea50c53a00848315833c1f34bf8f4a47f11a14499ae3f
2.14.1,737b430fac6caef7c485c9c47f0f9104,3aeb386c7ada3bd936bc20698b6d64e4e1643293,84057480ba7da6fb6d9ea50c53a00848315833c1f34bf8f4a47f11a14499ae3f |
JndiLookup.class for Log4J version,md5sum,sha1sum,sha256sum
2.0-beta9,662118846c452c4973eca1057859ad61,9799470c2cca80f047f6b0d1588dacae9aae26fc,39a495034d37c7934b64a9aa686ea06b61df21aa222044cc50a47d6903ba1ca8
2.0-rc1,662118846c452c4973eca1057859ad61,9799470c2cca80f047f6b0d1588dacae9aae26fc,39a495034d37c7934b64a9aa686ea06b61df21aa222044cc50a47d6903ba1ca8
2.0-rc2,1daf21d95a208cfce994704824f46fae,ec9326bae452f2d2e8a4852b24799d6458d11d46,a03e538ed25eff6c4fe48aabc5514e5ee687542f29f2206256840e74ed59bcd2
2,62c82ad7c1ec273a683de928c93abbe9,e605ca8be62f8f26c43d906f392090231e96edfd,fd6c63c11f7a6b52eff04be1de3477c9ddbbc925022f7216320e6db93f1b7d29
2.0.1,2365c12b4a7c5fa5d7903dd90ca9e463,040c7583735f58988635563b0b6c0f009d5ae5c0,964fa0bf8c045097247fa0c973e0c167df08720409fd9e44546e0ceda3925f3e
2.0.2,5c727238e74ffac28315c36df27ef7cc,7d403e7e7208e4d9ebaf2b32ddc90a04170580c5,9626798cce6abd0f2ffef89f1a3d0092a60d34a837a02bbe571dbe00236a2c8c
2.1,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.2,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.3,8ededbb1646c1a4dd6cdb93d9a01f43c,1b0283f98e00f04be9b8cf655f881e767c8bb386,a768e5383990b512f9d4f97217eda94031c2fa4aea122585f5a475ab99dc7307
2.4,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.4.1,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.5,da195a29e34e02e9e4c6663ce0b8f243,fb5cf0c358b50de4fcf6dc09bcb0ff7eccf2843a,a534961bbfce93966496f86c9314f46939fd082bb89986b48b7430c3bea903f7
2.6,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.6.1,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.6.2,766bf6b755adee673838fdf968c15079,f76a5c3b6aa75faa3dbbee93d776334c32dd102b,e8ffed196e04f81b015f847d4ec61f22f6731c11b5a21b1cfc45ccbc58b8ea45
2.7,4618c4bea52a4e2e2693b7d91b019c71,9d62849523dc3efbbe8b289e34f7cd84a6c37275,cee2305065bb61d434cdb45cfdaa46e7da148e5c6a7678d56f3e3dc8d7073eae
2.8,fe963defc63d2df86d3d4e2f160939ab,2e81d183edf1a8951b13a2f62de86e71d97e0d14,66c89e2d5ae674641138858b571e65824df6873abb1677f7b2ef5c0dd4dbc442
2.8.1,fe963defc63d2df86d3d4e2f160939ab,2e81d183edf1a8951b13a2f62de86e71d97e0d14,66c89e2d5ae674641138858b571e65824df6873abb1677f7b2ef5c0dd4dbc442
2.8.2,641fd7ae76e95b35f02c55ffbf430e6b,f5f55d34272b0ed9971943c35857dbca092c990f,d4ec57440cd6db6eaf6bcb6b197f1cbaf5a3e26253d59578d51db307357cbf15
2.9.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.9.1,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.10.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.0,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.1,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.11.2,88568653545359ace753f19a72b18208,ff0abd9cf6f6b59208251ef1ea0ff1509eba1924,0f038a1e0aa0aff76d66d1440c88a2b35a3d023ad8b2e3bac8e25a3208499f7e
2.12.0,4cb3a0271f77c02fd2de3144a729ab70,1dee0b0a29a7a2c13d4a7a12374038616cc1de89,5c104d16ff9831b456e4d7eaf66bcf531f086767782d08eece3fb37e40467279
2.12.1,4cb3a0271f77c02fd2de3144a729ab70,1dee0b0a29a7a2c13d4a7a12374038616cc1de89,5c104d16ff9831b456e4d7eaf66bcf531f086767782d08eece3fb37e40467279
2.13.0,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.1,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.2,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.13.3,7b2cf8f2e9d85014884add490878a600,0d502b6db6947e5b0c82725a65d719f0a8b16564,2b32bfc0556ea59307b9b2fde75b6dfbb5bf4f1d008d1402bc9a2357d8a8c61f
2.14.0,737b430fac6caef7c485c9c47f0f9104,3aeb386c7ada3bd936bc20698b6d64e4e1643293,84057480ba7da6fb6d9ea50c53a00848315833c1f34bf8f4a47f11a14499ae3f
2.14.1,737b430fac6caef7c485c9c47f0f9104,3aeb386c7ada3bd936bc20698b6d64e4e1643293,84057480ba7da6fb6d9ea50c53a00848315833c1f34bf8f4a47f11a14499ae3f






