Posted: August 14th, 2024 | Author: xanda | Filed under: Cinta Malaysia, IT Related | Tags: SEO | 1 Comment »
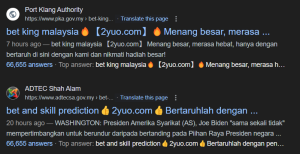
Executive Summary
Recent observations have uncovered a campaign targeting government websites globally, with a focus on those utilizing various content management systems (CMS), including Joomla. The attackers’ primary objective is to perform black hat SEO poisoning, manipulating search engine rankings to lure unsuspecting users to gambling websites. Notably, some defacers have shifted to this TTP, becoming affiliates of gambling, casino, and scam syndicates. This report details the tactics, techniques, and procedures (TTPs) observed in these attacks and provides recommendations for mitigating this threat.
Attack Overview
The attackers exploit vulnerabilities in outdated CMS platforms and plugins to gain unauthorized access to government websites. These sites are targeted due to their inherent high ranking in search engine results, making them ideal for SEO poisoning. It is important to note that this is not a sophisticated attack but rather an opportunistic exploitation of common vulnerabilities.
Tactics, Techniques, and Procedures (TTPs)
- Initial Compromise: The attackers leverage known vulnerabilities in various CMS platforms (and the plugins), such as Joomla, to infiltrate the target websites.
- Payload Delivery: Upon successful compromise, the attackers inject malicious scripts designed to manipulate search engine results.
- User Agent and Referer Checks:
- If the visitor’s user agent matches that of a Google-bot or originates from a Google IP, the site serves content optimized for SEO manipulation.
- If the visitor arrives via a Google search referer, additional checks (e.g., mobile vs. non-mobile user agents) are performed before redirecting the user to a Traffic Distribution System (TDS).
- Visitors from non-Google referers, blacklisted IPs, or geofenced regions are served a 404 “error” page.
- Traffic Distribution System (TDS): The TDS performs further checks and redirects the user to gambling or casino (or the current active subscription) portals.
Recommendations
For System Administrators:
-
- Update CMS and Plugins: Ensure all CMS platforms and plugins are regularly updated to mitigate known vulnerabilities.
- Implement Web Application Firewalls (WAF): Deploy WAFs to filter and monitor HTTP traffic, providing an additional layer of security.
- Monitor File Integrity: Regularly check for unauthorized changes to files and maintain system integrity through continuous monitoring.
For End Users:
-
- Exercise Caution with Search Results: Be vigilant when clicking on links in search engine results, especially those leading to unfamiliar websites.
- Utilize Protective DNS Services: Use DNS services that offer protection against known TDS and malicious websites.
For Regulators:
-
- Active Monitoring: Continuously monitor for malicious activities and black hat SEO attempts.
- Block Shady Sites: Proactively block access to known gambling and casino websites, which in this case, it could be scam as well, sorry i don’t validate.
- Mitigate TDS: Implement measures to block Traffic Distribution System domains used by attackers. Break the kill chain, and you don’t need to play a cat-and-mouse game with the final redirection domains.
Conclusion
The ongoing SEO poisoning attacks on government websites represent a significant threat to both web security and user safety. By understanding the TTPs employed by the attackers and implementing the recommended mitigation strategies, stakeholders can enhance their defenses against this evolving threat landscape.
Posted: May 7th, 2024 | Author: xanda | Filed under: IT Related | No Comments »

Imagine receiving an urgent SMS claiming to be from your bank. The message informs you that your credit card has been used for a suspicious transaction. To verify or dispute the charges, you’re instructed to call a provided phone number. Sounds familiar, right? No?

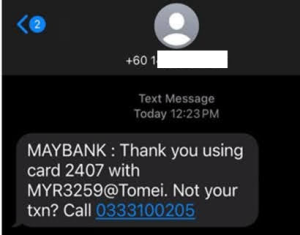
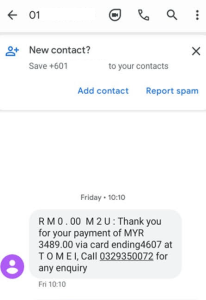
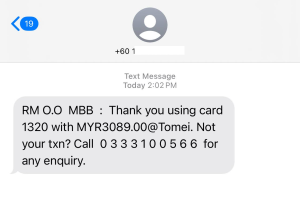
The SMS messages were sent from regular mobile phone numbers, not short code senders. Now, take a look at the phone numbers included in the SMS—they do not belong to the bank. Wait, look closely… What a neat sequence. Coincidence? :
- 0333100144
- 0333100566
- 0333100205
- 0329350072
- 0329350078
Earlier this morning, I decided to investigate further. I dialed the suspicious phone number, 0329350078, to understand the scammer’s modus operandi. To my surprise, an IVR system answered, claiming to represent Maybank. I selected the option to “report a suspicious transaction”, and the call was “transferred” to a real person. The person tried to convince me that my card and account had been hacked, and that it would be better to transfer the money to a third-party account before the account was frozen. I was eager to continue the conversation; however, I had a meeting to attend, so I terminated the call.
Later, around 6 p.m., I attempted to contact the same number once more, only to find it unreachable. Subsequently, I tried several other phone numbers, all of which proved to be similarly inaccessible.
A brief inquiry into the reputation (some) of these numbers suggests their involvement in shady activities over an extended period. While my intuition has provided some clues about the owners, I am not donning my investigative hat today, akin to Brian Krebs. Therefore, no disclosures will be made in this post.
Here are some advisory insights for awareness
How does it work:
- Victims receive an SMS claiming to be from a bank or financial institution
- The message typically warns of suspicious transactions on their account and provides a phone number to call
- When victims call the number, they are directed to an Interactive Voice Response (IVR) system that mimics the bank’s
- official system
- After selecting the option to report a suspicious transaction, victims are transferred to a real person who attempts to extract personal information or convince them to transfer money to a “safe account”
How to spot it:
- Be cautious if you receive unsolicited SMS messages related to your bank account/transaction – especially from normal mobile phone number. Banks will usually use short code SMS providers.
- Look for poor grammar, inconsistent formatting/spacing or spelling errors in the message (if any)
- Avoid clicking on any links provided in the SMS (URLs in SMS messages are now blocked in Malaysia, except when sent from a short code sender)
Protecting Yourself: Tips and Awareness
- Stay Informed: Be aware of common scams and their modus operandi. Familiarize yourself with the tactics fraudsters use to deceive victims.
- Verify Communications: If you receive an SMS or call related to your bank account, verify its legitimacy independently. Do not rely solely on the information provided in the message.
- Report Suspicious Activity: If you encounter a suspicious SMS or call, report it to your bank and NSRC (997) immediately.
- Educate Others: Share this information with family and friends to help them stay vigilant against scams.
Stay alert and safeguard yourself from falling prey to scams.
Posted: April 29th, 2024 | Author: xanda | Filed under: IT Related, Project | No Comments »
So, in my last blog post, you might’ve spotted something a bit different – an unintentional experiment with automation and LLM. Yep, it caught me off guard too.
But you know what? Despite the surprise, it got me thinking. And after a closer look, it turns out there’s something here worth exploring.
Seems like I can generate a “daily bulletin” using this method. So, I’m thinking of sticking with it for a while.
But let’s keep it real – human input is still crucial.
I’m open to your thoughts and suggestions. Any ideas on how to make this better? Just drop me a line.
Posted: April 28th, 2024 | Author: xanda | Filed under: IT Related | No Comments »

In recent years, Malaysia has witnessed a surge in “SMS” phishing (also known as smishing) attacks. These deceptive messages target unsuspecting individuals via text messages, luring them into revealing sensitive information or clicking on malicious links. Let’s delve into the key aspects of this growing threat:
1. The Prevalence of SMS Phishing
According to a survey conducted by international market research firm Ipsos, more than two-thirds of Malaysians (76%) have encountered scams at some point in their lives. Among the communication channels exploited by scammers, phone calls and WhatsApp applications take the lead. SMS phishing accounts for a significant portion, with 56% of respondents reporting such incidents. The remaining channels include Facebook (31%), Telegram (30%), and SMS text (29%).
2. Evolving Tactics
The modus operandi of SMS phishing has evolved over time. Initially, scammers targeted traditional SMS messages, but as telcos in Malaysia began blocking SMS containing URLs, fraudsters adapted. Recent campaigns have shifted focus to Apple iMessage and Android RCS (Rich Communication Services), which technically aren’t SMS but operate within similar messaging platforms. Additionally, spoofed SMS via fake base transceiver stations (BTS) have emerged, further complicating the landscape.
3. The TNG eWallet Scam
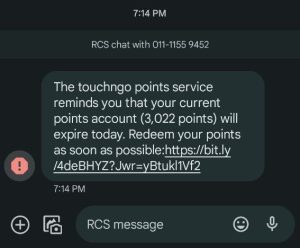
Recently, the theme of SMS phishing has shifted from parcel services and telco-related scams to TNG eWallet. Victims receive messages claiming that their loyalty points are about to expire, urging them to redeem by clicking a link. However, these links lead to fraudulent websites designed to steal personal information, including campaigns aimed at hijacking Telegram accounts. The shift to TNG eWallet reflects scammers’ adaptability and their ability to exploit popular services.
4. Reporting and Awareness
Despite the prevalence of SMS phishing, fewer than half of victims report the incidents to authorities. The police receive the majority of complaints (62%), while other agencies like the Malaysian Communications and Multimedia Commission (MCMC), CyberSecurity Malaysia, and Bank Negara Malaysia receive fewer reports. Raising awareness and empowering the public with education and digital safeguards are crucial steps in combating this menace.
5. Indicators of Compromise
Indicators of Compromise (IOCs) for the latest campaign should include relevant and enriched indicators:
touchngo-z.top
globeih.top
globein.top
telkomsel-og.top
telkomsel-oj.top
maxis-l.top
globeig.top
emag-k.top
telkomsel-om.top
telkomsel-ok.top
ais-g.top
ais-h.top
ais-f.top
ais-d.top
globeij.top
etisalat-z.top
telkomsel-oz.top
telkomsel-on.top
telkomsel-ox.top
telkomsel-ov.top
telkomsel-os.top
telkomsel-oq.top
telkomsel-id.com
dpd-a.top
emag-q.top
dpd-c.xyz
dpd-a.vip
globeif.top
globeiv.top
globeix.top
globeid.top
globeia.top
globeic.top
globeiz.top
globeib.top
globeis.top
emag-w.top
telkomseip.top
telkomseie.top
telkomseit.top
telkomseiw.top
telkomsexx.top
telkomseiq.top
telkomseir.top
telkomseiy.top
telkomsexz.top
telkomsexc.top
telkomseio.top
telkomsexv.top
telkomseiu.top
maltapost-x.top
telkomselia.top
telkomselic.top
cambodiapostv.top
telkomselim.top
telkomselil.top
telkomselib.top
telkomselik.top
telkomselij.top
ais-j.top
telkomselin.top |
touchngo-z.top
globeih.top
globein.top
telkomsel-og.top
telkomsel-oj.top
maxis-l.top
globeig.top
emag-k.top
telkomsel-om.top
telkomsel-ok.top
ais-g.top
ais-h.top
ais-f.top
ais-d.top
globeij.top
etisalat-z.top
telkomsel-oz.top
telkomsel-on.top
telkomsel-ox.top
telkomsel-ov.top
telkomsel-os.top
telkomsel-oq.top
telkomsel-id.com
dpd-a.top
emag-q.top
dpd-c.xyz
dpd-a.vip
globeif.top
globeiv.top
globeix.top
globeid.top
globeia.top
globeic.top
globeiz.top
globeib.top
globeis.top
emag-w.top
telkomseip.top
telkomseie.top
telkomseit.top
telkomseiw.top
telkomsexx.top
telkomseiq.top
telkomseir.top
telkomseiy.top
telkomsexz.top
telkomsexc.top
telkomseio.top
telkomsexv.top
telkomseiu.top
maltapost-x.top
telkomselia.top
telkomselic.top
cambodiapostv.top
telkomselim.top
telkomselil.top
telkomselib.top
telkomselik.top
telkomselij.top
ais-j.top
telkomselin.top
Posted: June 12th, 2023 | Author: xanda | Filed under: IT Related | No Comments »
Top 5 source of IPs for few protocols, hitting my honeypot last week (5-11 June 2023)
Apache:
153,143.110.222.166
143,77.68.98.209
127,80.211.51.121
127,54.36.102.11
127,182.16.248.237 |
153,143.110.222.166
143,77.68.98.209
127,80.211.51.121
127,54.36.102.11
127,182.16.248.237
SSH:
1757,180.242.128.226
1008,179.166.57.219
670,202.161.190.82
246,171.244.53.224
164,57.128.113.49 |
1757,180.242.128.226
1008,179.166.57.219
670,202.161.190.82
246,171.244.53.224
164,57.128.113.49
DNS:
17,47.100.101.182
4,71.6.199.23
3,45.128.232.145
3,185.94.111.1
3,152.32.200.113 |
17,47.100.101.182
4,71.6.199.23
3,45.128.232.145
3,185.94.111.1
3,152.32.200.113
Few IPs observed coming from Malaysian ISP
4788 | 210.187.80.132 | TMNET-AS-AP TM Net, Internet Service Provider, MY
9930 | 211.24.12.162 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
9930 | 211.25.119.142 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
23678 | 27.131.36.170 | MYKRIS-AS-MY Mykris Asia, Managed Network and Service Provider, MY |
4788 | 210.187.80.132 | TMNET-AS-AP TM Net, Internet Service Provider, MY
9930 | 211.24.12.162 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
9930 | 211.25.119.142 | TTNET-MY TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Alam Selangor, Malaysia, MY
23678 | 27.131.36.170 | MYKRIS-AS-MY Mykris Asia, Managed Network and Service Provider, MY
If you like to see the complete data captured within last week, you may visit the github page







