Ongoing SEO Poisoning Attacks on Government Websites
Posted: August 14th, 2024 | Author: xanda | Filed under: Cinta Malaysia, IT Related | Tags: SEO | 1 Comment »Executive Summary
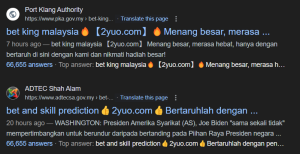
Recent observations have uncovered a campaign targeting government websites globally, with a focus on those utilizing various content management systems (CMS), including Joomla. The attackers’ primary objective is to perform black hat SEO poisoning, manipulating search engine rankings to lure unsuspecting users to gambling websites. Notably, some defacers have shifted to this TTP, becoming affiliates of gambling, casino, and scam syndicates. This report details the tactics, techniques, and procedures (TTPs) observed in these attacks and provides recommendations for mitigating this threat.
Attack Overview
The attackers exploit vulnerabilities in outdated CMS platforms and plugins to gain unauthorized access to government websites. These sites are targeted due to their inherent high ranking in search engine results, making them ideal for SEO poisoning. It is important to note that this is not a sophisticated attack but rather an opportunistic exploitation of common vulnerabilities.
Tactics, Techniques, and Procedures (TTPs)
- Initial Compromise: The attackers leverage known vulnerabilities in various CMS platforms (and the plugins), such as Joomla, to infiltrate the target websites.
- Payload Delivery: Upon successful compromise, the attackers inject malicious scripts designed to manipulate search engine results.
- User Agent and Referer Checks:
- If the visitor’s user agent matches that of a Google-bot or originates from a Google IP, the site serves content optimized for SEO manipulation.
- If the visitor arrives via a Google search referer, additional checks (e.g., mobile vs. non-mobile user agents) are performed before redirecting the user to a Traffic Distribution System (TDS).
- Visitors from non-Google referers, blacklisted IPs, or geofenced regions are served a 404 “error” page.
- Traffic Distribution System (TDS): The TDS performs further checks and redirects the user to gambling or casino (or the current active subscription) portals.
Recommendations
For System Administrators:
-
- Update CMS and Plugins: Ensure all CMS platforms and plugins are regularly updated to mitigate known vulnerabilities.
- Implement Web Application Firewalls (WAF): Deploy WAFs to filter and monitor HTTP traffic, providing an additional layer of security.
- Monitor File Integrity: Regularly check for unauthorized changes to files and maintain system integrity through continuous monitoring.
For End Users:
-
- Exercise Caution with Search Results: Be vigilant when clicking on links in search engine results, especially those leading to unfamiliar websites.
- Utilize Protective DNS Services: Use DNS services that offer protection against known TDS and malicious websites.
For Regulators:
-
- Active Monitoring: Continuously monitor for malicious activities and black hat SEO attempts.
- Block Shady Sites: Proactively block access to known gambling and casino websites, which in this case, it could be scam as well, sorry i don’t validate.
- Mitigate TDS: Implement measures to block Traffic Distribution System domains used by attackers. Break the kill chain, and you don’t need to play a cat-and-mouse game with the final redirection domains.
Conclusion
The ongoing SEO poisoning attacks on government websites represent a significant threat to both web security and user safety. By understanding the TTPs employed by the attackers and implementing the recommended mitigation strategies, stakeholders can enhance their defenses against this evolving threat landscape.
Nice write up . Thanks!