Posted: April 2nd, 2014 | Author: xanda | Filed under: IT Related | Tags: cld, cld2, ubuntu | 5 Comments »
I’ve been using chromium-compact-language-detector before, and when they moved to v2.0, chromium-compact-language-detector has been renamed in to Compact Language Detection 2 (CLD2). I’ve read blog post on the performance review and i’m really impressed. So let give them a try.
Install the dependencies:
sudo apt-get install mercurial gcc-multilib python-dev build-essential |
sudo apt-get install mercurial gcc-multilib python-dev build-essential
Download CLD2 and the python binding:
cd /tmp/
svn checkout http://cld2.googlecode.com/svn/trunk/ cld2
hg clone https://code.google.com/p/chromium-compact-language-detector/ |
cd /tmp/
svn checkout http://cld2.googlecode.com/svn/trunk/ cld2
hg clone https://code.google.com/p/chromium-compact-language-detector/
Compile CLD2 and install the lib (for 32bit) :
cd /tmp/cld2/internal/
cat compile_libs.sh | sed 's/\ \-m64\ //g' > compile_me.sh
chmod +x compile_me.sh
./compile_me.sh
sudo cp *.so /usr/lib/ |
cd /tmp/cld2/internal/
cat compile_libs.sh | sed 's/\ \-m64\ //g' > compile_me.sh
chmod +x compile_me.sh
./compile_me.sh
sudo cp *.so /usr/lib/
Compile CLD2 and install the lib (for 64bit) :
cd /tmp/cld2/internal/
./compile_libs.sh
sudo cp *.so /usr/lib64/ |
cd /tmp/cld2/internal/
./compile_libs.sh
sudo cp *.so /usr/lib64/
Compile the python binding:
cd /tmp/chromium-compact-language-detector/
python setup.py build
python setup_full.py build
sudo python setup.py install
sudo python setup_full.py install |
cd /tmp/chromium-compact-language-detector/
python setup.py build
python setup_full.py build
sudo python setup.py install
sudo python setup_full.py install
Give the library a test:
For documentation:
python -c "import cld2; help(cld2.detect)" |
python -c "import cld2; help(cld2.detect)"
Done! Thanks
Posted: October 24th, 2013 | Author: xanda | Filed under: IT Related | Tags: macports, Mavericks | 1 Comment »
Quick update for those who found something buggy with their Macports after upgraded their OSX to Mavericks
- Download and install Xcode 5.0.1
- Install Command Line Tool
- Accept Xcode license agreement
- Download Macports source
cd /tmp
wget https://distfiles.macports.org/MacPorts/MacPorts-2.2.0.tar.gz |
cd /tmp
wget https://distfiles.macports.org/MacPorts/MacPorts-2.2.0.tar.gz
- Extract and compile
tar xvfz MacPorts-2.2.0.tar.gz
cd MacPorts-2.2.0
./configure
make
sudo make install |
tar xvfz MacPorts-2.2.0.tar.gz
cd MacPorts-2.2.0
./configure
make
sudo make install
- Update your Macports
Thanks
Posted: May 13th, 2013 | Author: xanda | Filed under: IT Related | Tags: placeholder, typo squatting | 1 Comment »
I’ve been monitoring placeholder and typo squatting domains for few months now, and I’ve read a write-up on ISC diary on “Is there an epidemic of typo squatting?”. There are a few conclusions that I can make and share:
- Most of typo squatting domains are parked on two /24 network, and by default, they are serving placeholder on the main page
- The page (content) is detected by McAfee as JS/Redirector.ar or JS/Blacole-Redirect
- There are a lot of domains (typo squatting some famous big websites) have been bought/rent, and used in Scam (win an iPad, win a voucher) activities.
- Beside of Scam activities as in No 3, I’ve also seen domains that have been used in serving malicious content/redirection.
- Speaking about item no 4, one interesting point to share is, after serving the malicious content/redirection for some time (mostly 1 or 2 weeks), the domain will be pointed back to the placeholder server and serving the placeholder again
- Item 4, and 5 also applicable for Phishing activities
- In the last couple of days (or week), they’ve started to ‘hide’ themself behind CloudFlare IPs.
- Today (or maybe it happened in the weekend), a few IPs have changed their default interface (of the placeholder) into some plain page with something like “what are you looking for?” message.
Seeing something similar or totally different? Feel free to share your points in the comment section.
Thanks
Posted: April 5th, 2013 | Author: xanda | Filed under: IT Related | No Comments »
Have you ever came across the following line of code injected to your (or you visited) website
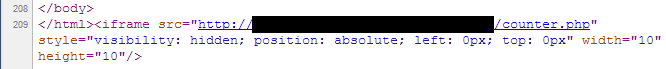
If I get it correctly, it is the BlackHole Exploit Kit redirector.
The pattern for this “counter.php” injected script will always be the same, so for system administrator or webmasters, you can use the following yara rule for your detection
rule counterPHPredirectBHEK
{
meta:
author = "adnan.shukor@gmail.com"
description = "Detection rule to detect compromised page injected with invisible counter.php redirector"
ref = "http://blog.xanda.org/2013/04/05/detecting-counter-php-the-blackhole-redirector"
cve = "NA"
version = "1"
impact = 4
hide = false
strings:
$counterPHP = /\<iframe\ src\=\"https?\:\/\/[a-zA-Z0-9\-\.]{4,260}\/counter\.php\"\ style\=\"visibility\:\ hidden\;\ position\:\ absolute\;\ left\:\ 0px\;\ top\:\ 0px\"\ width\=\"10\"\ height\=\"10\"\/\>$/
condition:
all of them
} |
rule counterPHPredirectBHEK
{
meta:
author = "adnan.shukor@gmail.com"
description = "Detection rule to detect compromised page injected with invisible counter.php redirector"
ref = "http://blog.xanda.org/2013/04/05/detecting-counter-php-the-blackhole-redirector"
cve = "NA"
version = "1"
impact = 4
hide = false
strings:
$counterPHP = /\<iframe\ src\=\"https?\:\/\/[a-zA-Z0-9\-\.]{4,260}\/counter\.php\"\ style\=\"visibility\:\ hidden\;\ position\:\ absolute\;\ left\:\ 0px\;\ top\:\ 0px\"\ width\=\"10\"\ height\=\"10\"\/\>$/
condition:
all of them
}
Thanks
P/S: MyYaraSIG guys, my Macbook is not able to be boot right now, will commit to the repo later
Posted: February 15th, 2013 | Author: xanda | Filed under: IT Related | No Comments »
Hi,
Nothing special and interesting but just to share some (old) info on this topic
I’ve read Sophos’s blog post yesterday on “Malware injected into legitimate JavaScript code on legitimate websites” and it seems like a familiar stuff to me. I’ve also been asked in the comment section of “RedKit Patterns – Additional Info to @fknsec Writeup” entry on something that is related to this issue so lets just blog about it
I’ve performed a quick search in URLquery and managed to get these samples:
- hxxp://www.nedakitap.com/js/jquery[dot]js
- hxxp://www.nedakitap.com/js/jquery.carouFredSel-5.5.0-packed[dot]js
You may found more sample of there. The point is there is no specific version of jquery targeted (as asked in the comment section) since in order for you to modify/edit the jquery file, you need to have the CMS/server compromised in the first place and jquery is not a CMS 🙂 . However, by looking at the version of the jquery, you will be able to predict the ‘age’ of the CMS used and the last update date. Mostly they are old (meaning that the CMS is not updated)

Viewing the content of the modified/compromised JavaScript file (in this example, jquery) you can see the additional code in line no 1, (2 is a empty line), 3, second last, and last line of the JavaScript file. And the pattern will always be the same.

The JavaScript files which have been called will execute the injected script and write an (almost) invisible iframe redirecting victim to another compromised website which is hosting RedKit exploit kit. Most of the time, the host with the compromised JS will also have the RedKit files on it and waiting to be called by another compromised JS on another website
Some other characteristics that can help you to determine these injected code are by looking at these keywords:
- iframe
- name=Twitter
- scrolling=auto
- frameborder=no
- align=center
- height=2
- width=2
- a .htm or .html file in the web root directory in 4 char length and sometime came with query variable of ‘h’, ‘i’ or ‘j’ **scroll below to see update on 7 Mar**
Lets make a conclusion and write a simple regex for this
document\.write\('<iframe\ name=Twitter\ scrolling=auto\ frameborder=no\ align=center\ height=2\ width=2\ src=http:\/\/[\w\.\-]{4,}\/[a-z]{4}\.html?(\?[hij]=\d{7})?><\/iframe>'\); |
document\.write\('<iframe\ name=Twitter\ scrolling=auto\ frameborder=no\ align=center\ height=2\ width=2\ src=http:\/\/[\w\.\-]{4,}\/[a-z]{4}\.html?(\?[hij]=\d{7})?><\/iframe>'\);
Once you have 4 hits, you know it is RedKit redirector.
Yes you can modify it to be used as yara signature as well 🙂
Thats all from me for now
Thanks and stay safe
** Updated on 16 Feb **
According to Securi, this is a family of TDS
** Updated on 7 Mar **
Found new pattern that use PHP.. A quick yara rule would be:
rule iframeRedKit
{
meta:
author = "adnan.shukor@gmail.com"
description = "Detection rule to detect compromised page injected with invisible iframe of Redkit redirector"
ref = "http://blog.xanda.org/2013/02/15/redkit-redirector-injected-into-legitimate-javascript-code/"
cve = "NA"
version = "1.2"
impact = 4
hide = false
strings:
$iRedKit_1 = /name\=['"]?Twitter['"]?/
$iRedKit_2 = /scrolling\=['"]?auto['"]?/
$iRedKit_3 = /frameborder\=['"]?no['"]?/
$iRedKit_4 = /align\=['"]?center['"]?/
$iRedKit_5 = /height\=['"]?2['"]?/
$iRedKit_6 = /width\=['"]?2['"]?/
$iRedKit_7 = /src\=['"]?http:\/\/[\w\.\-]{4,}\/(([a-z]{4}\.html?(\?[hij]=\d{7})?)|([a-z]{4,}\.php\?[a-z]{4,}\=[a-f0-9]{16}))['"]?/
condition:
all of them
} |
rule iframeRedKit
{
meta:
author = "adnan.shukor@gmail.com"
description = "Detection rule to detect compromised page injected with invisible iframe of Redkit redirector"
ref = "http://blog.xanda.org/2013/02/15/redkit-redirector-injected-into-legitimate-javascript-code/"
cve = "NA"
version = "1.2"
impact = 4
hide = false
strings:
$iRedKit_1 = /name\=['"]?Twitter['"]?/
$iRedKit_2 = /scrolling\=['"]?auto['"]?/
$iRedKit_3 = /frameborder\=['"]?no['"]?/
$iRedKit_4 = /align\=['"]?center['"]?/
$iRedKit_5 = /height\=['"]?2['"]?/
$iRedKit_6 = /width\=['"]?2['"]?/
$iRedKit_7 = /src\=['"]?http:\/\/[\w\.\-]{4,}\/(([a-z]{4}\.html?(\?[hij]=\d{7})?)|([a-z]{4,}\.php\?[a-z]{4,}\=[a-f0-9]{16}))['"]?/
condition:
all of them
}


