Posted: September 8th, 2012 | Author: xanda | Filed under: IT Related | Tags: defacement, internet explorer, merdeka, MS12-052, yara | No Comments »
This week I’ll be writing on a short update related to Malaysia merdeka (independence) day and Internet Explorer MS12-052 bug.
It is almost like a tradition here, in Malaysia, to receive a massive number of system intrusion and website defacement on our merdeka (independence) day. Based on the data of the previous years, most of the attacks came from the foreign countries, and the messages left by them clearly reflect their political motive on performing the attack.
But in 2012, the incidents landscape on the merdeka day (week) shifted. The total number of system intrusion and website defacement reduced a lot compare to the same period of time in the previous years. This data can be verified by performing zone-h search, and you can cross check your findings with MyCERT monthly statistic by end of this month (or early next month).
One thing that is sad to be shared here is, it is not only the number that has shifted, the source of attack for this year is also showing some differences. Most of the defacement cases this year, that is related to .MY domain, or websites that are hosted in the IP range of Malaysia, were performed mostly by local attackers. Their messages are not clear, but a quick conclusion that I can make is, it was for fame.
Also in this week’s update, I’ll cover a bit on the “Internet Explorer Script Interjection Code Execution (updated)” that has been posted to Bugtraq mailing list. You can read the details part of the advisory in the “VULNERABILITY DETAILS” section. As of the writing of this update, there is no news yet on this vulnerability (MS12-052) has been used in the wild, and I’ve cross checked with Metasploit and confirmed that, it is not yet ported to Metasploit. However, with the detail explanation provided in the advisory, I don’t think it will take any longer for the working exploit to be made public.
You can use the following generic Yara rule to detect a malicious html/JS file exploiting this vulnerability:
rule MS12_052
{
meta:
author = "Adnan Mohd Shukor"
author_email = "adnan.shukor @ G!"
ref = "MS12-052"
ref_url = "http://seclists.org/bugtraq/2012/Sep/29"
cve = "CVE-"
version = "1"
impact = 4
hide = false
strings:
$ms12052_1 = /mailto\:.{2000,}/ nocase fullword
$ms12052_2 = /\.getElements?By/ nocase
$ms12052_3 = /\.removeChild\(/ nocase
$ms12052_4 = /document\..*?= ?null/ nocase
condition:
$ms12052_1 and $ms12052_2 and ($ms12052_3 or $ms12052_4)
} |
rule MS12_052
{
meta:
author = "Adnan Mohd Shukor"
author_email = "adnan.shukor @ G!"
ref = "MS12-052"
ref_url = "http://seclists.org/bugtraq/2012/Sep/29"
cve = "CVE-"
version = "1"
impact = 4
hide = false
strings:
$ms12052_1 = /mailto\:.{2000,}/ nocase fullword
$ms12052_2 = /\.getElements?By/ nocase
$ms12052_3 = /\.removeChild\(/ nocase
$ms12052_4 = /document\..*?= ?null/ nocase
condition:
$ms12052_1 and $ms12052_2 and ($ms12052_3 or $ms12052_4)
}
Thats all for this week.
Thanks
Posted: August 27th, 2012 | Author: xanda | Filed under: IT Related | 2 Comments »
Earlier today, FireEye, DeepEndResearch and AlienVault has posted on their blog regarding their findings on the recent JRE 1.7 0day exploit. Within seconds, @jduck1337 has came out with the PoC of the exploit and later it has been ported and made public by Metasploit
While waiting for the patch (from Oracle) to be available, users are highly recommended to disable the Java support in their browser. Java support can be disabled by:
- For Internet Explorer user
- Click Tools and then Internet Options
- Select the Security tab, and select the Custom Level button
- Scroll down to Scripting of Java applets
- Make sure the Enable radio button is unchecked
- Click OK to save your preference
- For Google Chrome user
- Click on the wrench icon, then select Options.
- Select Under the Hood and then Privacy Content Settings.
- The Content Settings panel will appear.
- In the Plug-ins section, select the Disable individual plug-ins link to check whether Java is enabled
- Click on the Disable link (if the Enable link appears, Java is already disabled)
- For Mozilla Firefox user
- Start Mozilla Firefox browser
- At the top of the browser, select the Firefox button (or Tools menu in Windows XP), then Add-ons
- The Add-ons Manager tab will open.
- In the Add-ons Manager tab, select Plugins
- Click Java (TM) Platform plugin to select it
- Click on the Disable button (if the button says Enable, Java is already disabled)
- For Safari user
- Launch Safari browser
- Click on Safari and select Preferences
- Click on the Security tab
- Uncheck (unselect) Enable Java check box
- Close Safari Preferences window
Stay safe. Bye
Reference: http://java.com/en/download/help/enable_browser.xml
Posted: August 25th, 2012 | Author: xanda | Filed under: IT Related | No Comments »
Hi everyone and Eid Mubarak to my Muslim friends.
If you haven’t heard about A.R.E. yet, it is basically The Android Reverse Engineering (A.R.E.) Virtual Machine that combines the latest Android malware analysis tools in a readily accessible toolbox.
Tools currently found on A.R.E. are:
A github repo created by the A.R.E maintainer for easy installation and update, however the rapid development of each individual project above, does not sync with the update of the A.R.E github repo. This is why AREsoft-updater was created.
AREsoft-updater is an updater script for Android Reverse Engineering Software belongs to ARE VM from the Honeynet Project
AREsoft-updater will check for the latest available version of each individual project/tool listed above and compare it with the local (installed) version in A.R.E. If newer version is available, AREsoft-updater will automatically download and install the update for your A.R.E
AREsoft-updater also support the latest (recently released) DroidBox for Android 2.3 and APIMonitor
AREsoft-updater will require curl to work. Kindly install curl in your A.R.E virtual machine
AREsoft-updater is released under WTFPL (Do What The Fuck You Want To Public License) at my github https://github.com/xanda/AREsoft-updater
Thanks
Posted: August 10th, 2012 | Author: xanda | Filed under: IT Related | 1 Comment »
Hi and Ramadan Mubarak to my Muslim friends.
Last few night I saw a twitter update from @pentestit on a project called PHP-Shell-Detector; a php script that helps you find and identify php/cgi(perl)/asp/aspx shells.
My friends and I were a bit disappointed because we have developed the same thing but not yet released to the public for no reason.
But speaking about PHP-Shell-Detector, new stuff still need to be tested 🙂 so I’ve put it into a test
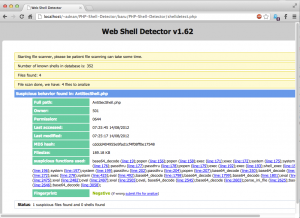
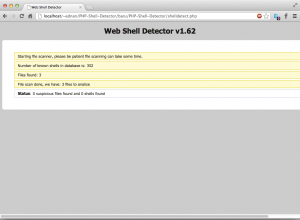
I’ve tested with a webshell I’ve found in the wild. Impressive.. PHP-Shell-Detector managed to detect it. The GUI and ajax was nice as well
I’ve spent some time to take a look at the code and found that the “suspicious functions used” part was implemented with the use of regex and I’ve found that something is missing.. So i’ve created a simple webshell to test my theory. So here is my code:
<?php
$cmd = $_GET['cmd'];
echo `$cmd`;
?> |
<?php
$cmd = $_GET['cmd'];
echo `$cmd`;
?>
And lets see the result:
This is due to the backtick is not in the regex and I believe it is not in the signature part as well.
I’ve reported this issue on the github page and comeout with the regex and tokenizer suggestion as the solution but from the response that i’ve get, i dont think it will be implemented in this near soon.
Anyway.. As overall, PHP-Shell-Detector is a good project and would help the webmaster to simplify the process of “searching” the hidden planted shell in their website.
Thanks
[Update]
I’ve received an email from the project maintainer saying that the regex has been update. Awesome! 🙂
Posted: August 2nd, 2012 | Author: xanda | Filed under: IT Related | Tags: 64bit, Android, emulator, ubuntu | No Comments »
SDL init failure, reason is: No available video device |
SDL init failure, reason is: No available video device
If you are getting the above error while launching Android emulator on 64bit OS, these are what you need to do:
sudo apt-get update
sudo apt-get install ia32-libs |
sudo apt-get update
sudo apt-get install ia32-libs
Thats all.. Now relaunch you emulator.
Thanks
Updated on 7th August 2012
Here is another tips for you on How to Start Intel Hardware-assisted Virtualization (hypervisor) on Linux to Speed-up Intel Android x86 Gingerbread Emulator