Posted: September 10th, 2009 | Author: xanda | Filed under: IT Related | Tags: bypass, plugin, proxy, TM | 13 Comments »

Hi all especially TM staffs 😛
I’ve wrote a Firefox plugin that helps you (TM staffs) to bypass the TM proxy and allow you to browse Facebook and Twitter from TM’s internal network or via TM’s secure VPN.
The plugin now is in BETA version and version 1.1 (release version) will be distributed tonight.
This plugin will be released in controlled copy where ONLY those person that I knew and those in my trusted group of people will get it.
Greetz and thanks to my BETA tester: Azra, Farah and Fathi
Posted: September 2nd, 2009 | Author: xanda | Filed under: IT Related | Tags: begin, curb, curl, error, HostResolutionError, rescue, ruby | No Comments »
The following error occur when executing the following code WITH NO internet connection

#!/usr/bin/ruby
require 'rubygems'
require 'curb' #yerp you need to sudo gem install curb
def browse(url)
c = Curl::Easy.new(url)
c.connect_timeout = 3
c.perform
return c.body_str
end
url = gets
puts browse(url) |
#!/usr/bin/ruby
require 'rubygems'
require 'curb' #yerp you need to sudo gem install curb
def browse(url)
c = Curl::Easy.new(url)
c.connect_timeout = 3
c.perform
return c.body_str
end
url = gets
puts browse(url)
So to handle the error in ruby, I’ll next time use “begin” and “rescue”
#!/usr/bin/ruby
require 'rubygems'
require 'curb' #yerp you need to sudo gem install curb
def browse(url)
c = Curl::Easy.new(url)
begin
c.connect_timeout = 3
c.perform
return c.body_str
rescue
return "Error in connection"
end
end
url = gets
puts browse(url) |
#!/usr/bin/ruby
require 'rubygems'
require 'curb' #yerp you need to sudo gem install curb
def browse(url)
c = Curl::Easy.new(url)
begin
c.connect_timeout = 3
c.perform
return c.body_str
rescue
return "Error in connection"
end
end
url = gets
puts browse(url)
Resulting:

Just a notes to myself and at the same time “snip” code for others
Posted: August 25th, 2009 | Author: xanda | Filed under: IT Related | Tags: client side, clientme, honeypot, preview | 2 Comments »
Don’t get me wrong.. It is not ready yet.. This is just the preview for one of the components



Posted: August 25th, 2009 | Author: xanda | Filed under: IT Related | Tags: acrobat, adobe, flash, unpatch | 2 Comments »
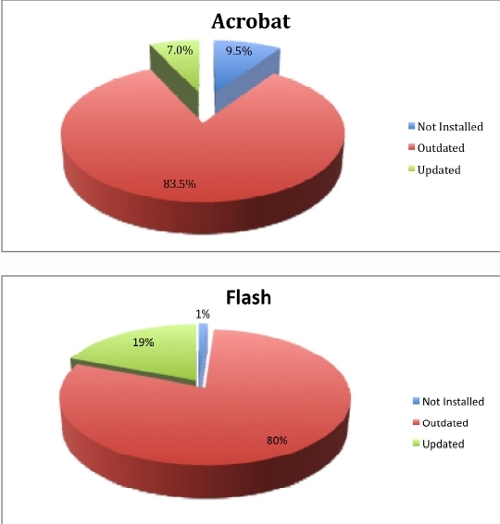
According to a research published by Trusteer earlier this month, 79.5% of the 2.5 million users of their Rapport security service run a vulnerable version of Adobe Flash, with 83.5% also running a vulnerable version of Acrobat.
The company has also criticized Adobe by insisting that their update mechanism “does not meet the requirements of a system that is used by 99% of users on the Internet and is highly targeted by criminals“, but is praising the update mechanism of Google’s Chrome and Firefox, whose silent updates close the window of opportunity for malicious attackers to take advantage of.
[Read more HERE]
Posted: August 25th, 2009 | Author: xanda | Filed under: IT Related | Tags: Cross Site Flashing, flash, XSF | No Comments »
A few days ago a lot of media wrote about a Flash worm. I managed to get hold of samples and analyzed it (thanks to Peter Kruse of CSIS for the samples).
First of all, while the exploit code contains Flash, it is actually just used as an attack (or, if we stretch it, infection) vector. The worm itself is contained in JavaScript and is very similar to the Twitter worm I analyzed back in April this year (see http://isc.sans.org/diary.html?storyid=6187). That is not surprising as both worms are attacking similar services.
The worm was first identified on a popular Chinese social web site (for schools, if I’m not wrong), Renren (http://www.renren.com). This site is in many ways similar to Twitter or Facebook, but much more media intensive and it allows users to share various information, including pictures, movies etc.
[Read more HERE]






