Posted: June 11th, 2010 | Author: xanda | Filed under: IT Related | Tags: adobe, CVE-2010-1297, flash, jsunpack, pdf, yara | 1 Comment »
rule FlashNewfunction: decodedPDF
{
meta:
ref = "CVE-2010-1297"
hide = true
impact = 5
strings:
$unescape = "unescape" fullword nocase
$shellcode = /%u[A-Fa-f0-9]{4}/
$shellcode5 = /(%u[A-Fa-f0-9]{4}){5}/
$cve20101297 = /\/Subtype ?\/Flash/
condition:
($unescape and $shellcode and $cve20101297) or ($shellcode5 and $cve20101297)
} |
rule FlashNewfunction: decodedPDF
{
meta:
ref = "CVE-2010-1297"
hide = true
impact = 5
strings:
$unescape = "unescape" fullword nocase
$shellcode = /%u[A-Fa-f0-9]{4}/
$shellcode5 = /(%u[A-Fa-f0-9]{4}){5}/
$cve20101297 = /\/Subtype ?\/Flash/
condition:
($unescape and $shellcode and $cve20101297) or ($shellcode5 and $cve20101297)
}
Posted: October 9th, 2009 | Author: xanda | Filed under: IT Related | Tags: 0day, acrobat, adobe, clientside, CVE-2009-3459, javascript, pdf | No Comments »

Nothing much but YES to agree with Didier Stevens with his statement:
PDF + JS = OMG
Yerp.. there is another vulnerability (CVE-2009-3459) in Adobe Reader and Acrobat today (GMT +8) and so far it is still 0 day..
*panic panic* What to do?
- Disable JavaScript support in Adobe Reader and Acrobat
- Enable DEP (for Windows)
- Use NoScript
- Use alternative PDF reader like Foxit, Gnome Document Viewer, yada yada..
- Don’t be a lame by opening unknown PDF attachment
Posted: August 25th, 2009 | Author: xanda | Filed under: IT Related | Tags: acrobat, adobe, flash, unpatch | 2 Comments »
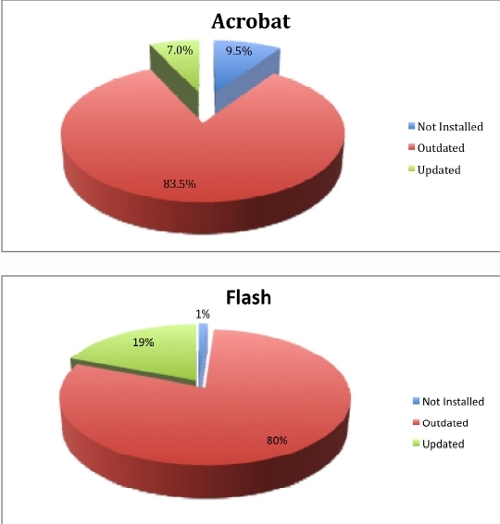
According to a research published by Trusteer earlier this month, 79.5% of the 2.5 million users of their Rapport security service run a vulnerable version of Adobe Flash, with 83.5% also running a vulnerable version of Acrobat.
The company has also criticized Adobe by insisting that their update mechanism “does not meet the requirements of a system that is used by 99% of users on the Internet and is highly targeted by criminals“, but is praising the update mechanism of Google’s Chrome and Firefox, whose silent updates close the window of opportunity for malicious attackers to take advantage of.
[Read more HERE]

