Posted: June 11th, 2010 | Author: xanda | Filed under: IT Related | Tags: adobe, CVE-2010-1297, flash, jsunpack, pdf, yara | 1 Comment »
rule FlashNewfunction: decodedPDF
{
meta:
ref = "CVE-2010-1297"
hide = true
impact = 5
strings:
$unescape = "unescape" fullword nocase
$shellcode = /%u[A-Fa-f0-9]{4}/
$shellcode5 = /(%u[A-Fa-f0-9]{4}){5}/
$cve20101297 = /\/Subtype ?\/Flash/
condition:
($unescape and $shellcode and $cve20101297) or ($shellcode5 and $cve20101297)
} |
rule FlashNewfunction: decodedPDF
{
meta:
ref = "CVE-2010-1297"
hide = true
impact = 5
strings:
$unescape = "unescape" fullword nocase
$shellcode = /%u[A-Fa-f0-9]{4}/
$shellcode5 = /(%u[A-Fa-f0-9]{4}){5}/
$cve20101297 = /\/Subtype ?\/Flash/
condition:
($unescape and $shellcode and $cve20101297) or ($shellcode5 and $cve20101297)
}
Posted: November 29th, 2009 | Author: xanda | Filed under: IT Related | Tags: analyz3r, client side, exploit, filter, hex, pdf | No Comments »
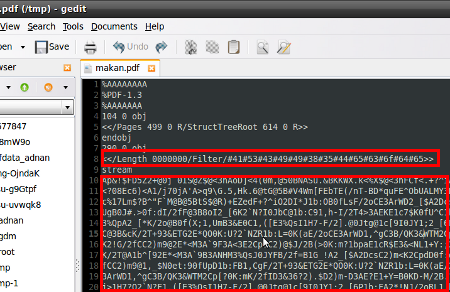
I was reading my RSS feed and suddenly I’ve found this PDF sample. We’ve found PDF-JS Obfuscation with this.info.title last week and this time comes another trick. Using hexadecimal in defining filter..
The following line was found in one of the stream
</Length 0000000/Filter/#41#53#43#49#49#38#35#44#65#63#6f#64#65>> |
</Length 0000000/Filter/#41#53#43#49#49#38#35#44#65#63#6f#64#65>>
once converted from hex to ascii, here is what i’ve found
</Length 0000000/Filter/ASCII85Decode>> |
</Length 0000000/Filter/ASCII85Decode>>
Yeah.. nothing much, but yes the sample will be passed to Azizan for enhancement of Analyz3r
Posted: October 9th, 2009 | Author: xanda | Filed under: IT Related | Tags: 0day, acrobat, adobe, clientside, CVE-2009-3459, javascript, pdf | No Comments »

Nothing much but YES to agree with Didier Stevens with his statement:
PDF + JS = OMG
Yerp.. there is another vulnerability (CVE-2009-3459) in Adobe Reader and Acrobat today (GMT +8) and so far it is still 0 day..
*panic panic* What to do?
- Disable JavaScript support in Adobe Reader and Acrobat
- Enable DEP (for Windows)
- Use NoScript
- Use alternative PDF reader like Foxit, Gnome Document Viewer, yada yada..
- Don’t be a lame by opening unknown PDF attachment

